Security News

A Chinese hacking group has breached the email accounts of more than two dozen organizations worldwide, including U.S. and Western European government agencies, according to Microsoft. "Microsoft investigations determined that Storm-0558 gained access to customer email accounts using Outlook Web Access in Exchange Online and Outlook.com by forging authentication tokens to access user email," Microsoft said in a blog post published late Tuesday evening.

Cybersecurity researchers have unearthed a novel rootkit signed by Microsoft that's engineered to communicate with an actor-controlled attack infrastructure. "This malicious actor originates from China and their main victims are the gaming sector in China," Trend Micro's Mahmoud Zohdy, Sherif Magdy, and Mohamed Fahmy said.

Sophisticated hackers have accessed email accounts of organizations and government agencies via authentication tokens they forged by using an acquired Microsoft account consumer signing key, the company has revealed on Tuesday. "The threat actor Microsoft links to this incident is an adversary based in China that Microsoft calls Storm-0558. We assess this adversary is focused on espionage, such as gaining access to email systems for intelligence collection."

Microsoft blocked code signing certificates predominantly used by Chinese hackers and developers to sign and load malicious kernel mode drivers on breached systems by exploiting a Windows policy loophole. With Windows Vista, Microsoft introduced policy changes restricting how Windows kernel-mode drivers could be loaded into the operating system, requiring developers to submit their drivers for review and sign them through Microsoft's developer portal.

A Microsoft Windows policy loophole has been observed being exploited primarily by native Chinese-speaking threat actors to forge signatures on kernel-mode drivers. "Actors are leveraging multiple open-source tools that alter the signing date of kernel mode drivers to load malicious and unverified drivers signed with expired certificates," Cisco Talos said in an exhaustive two-part report shared with The Hacker News.

HCA Healthcare disclosed a data breach impacting an estimated 11 million patients who received care at one of its hospitals and clinics after a threat actor leaked samples of the stolen data on a hacking forum.As first reported by DataBreaches.net, on July 5th, 2023, a threat actor began selling data allegedly belonging to HCA Healthcare on a forum used to sell and leak stolen data.

A threat actor referred to as 'RomCom' has been targeting organizations supporting Ukraine and guests of the upcoming NATO Summit set to start tomorrow in Vilnius, Lithuania. BlackBerry's research and intelligence team recently discovered two malicious documents that impersonated the Ukranian World Congress organization and topics related to the NATO Summit to lure selected targets.

Security researchers observed a new campaign they attribute to the Charming Kitten APT group where hackers used new NokNok malware that targets macOS systems. After gaining the target's trust, Charming Kitten sends a malicious link that contains a Google Script macro, redirecting the victim to a Dropbox URL. This external source hosts a password-protected RAR archive with a malware dropper that leverages PowerShell code and an LNK file to stage the malware from a cloud hosting provider.
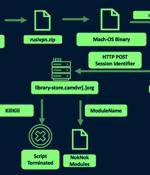
The Iranian nation-state actor known as TA453 has been linked to a new set of spear-phishing attacks that infect both Windows and macOS operating systems with malware. "TA453 eventually used a variety of cloud hosting providers to deliver a novel infection chain that deploys the newly identified PowerShell backdoor GorjolEcho," Proofpoint said in a new report.
An e-crime actor of Mexican provenance has been linked to an Android mobile malware campaign targeting financial institutions globally, but with a specific focus on Spanish and Chilean banks, from June 2021 to April 2023. "Despite using relatively unsophisticated tools, Neo Net has achieved a high success rate by tailoring their infrastructure to specific targets, resulting in the theft of over 350,000 EUR from victims' bank accounts and compromising Personally Identifiable Information of thousands of victims," Thill said.