Security News
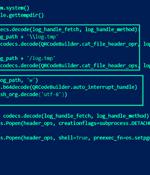
Three additional rogue Python packages have been discovered in the Package Index repository as part of an ongoing malicious software supply chain campaign called VMConnect, with signs pointing to the involvement of North Korean state-sponsored threat actors. First disclosed at the start of the month by the company and Sonatype, VMConnect refers to a collection of Python packages that mimic popular open-source Python tools to download an unknown second-stage malware.

New findings show that malicious actors could leverage a sneaky malware detection evasion technique and bypass endpoint security solutions by manipulating the Windows Container Isolation Framework. Microsoft's container architecture uses what's called a dynamically generated image to separate the file system from each container to the host and at the same time avoid duplication of system files.

Hackers are using a critical exploit chain to target Juniper EX switches and SRX firewalls via their Internet-exposed J-Web configuration interface. One week after Juniper disclosed and released security updates to patch the four flaws that can be chained to achieve remote code execution, watchTowr Labs security researchers released a proof-of-concept exploit targeting the SRX firewall bugs.

Unpatched Citrix NetScaler systems exposed to the internet are being targeted by unknown threat actors in what's suspected to be a ransomware attack. Attack chains involve the exploitation of CVE-2023-3519, a critical code injection vulnerability impacting NetScaler ADC and Gateway servers that could facilitate unauthenticated remote code execution.

Any clues as to what makes up the structure of a password is very helpful to hackers. We'll walk through how hackers take advantage of four of the most common password mistakes users make, as well as ways to strengthen your Active Directory against these risks.

Microsoft has identified a new hacking group it now tracks as Flax Typhoon that argets government agencies and education, critical manufacturing, and information technology organizations likely for espionage purposes. Operating since at least mid-2021, Flax Typhoon mainly targeted organizations in Taiwan, although Microsoft discovered some victims in Southeast Asia, North America, and Africa.

Two U.K. teenagers have been convicted by a jury in London for being part of the notorious LAPSUS$ transnational gang and for orchestrating a series of brazen, high-profile hacks against major tech firms and demanding a ransom in exchange for not leaking the stolen information. Central to pulling off the extortion schemes was their ability to conduct SIM swapping and prompt bombing attacks to gain unauthorized access to corporate networks after an extensive social engineering phase.

Ransomware threat actors are spending less time on compromised networks before security solutions sound the alarm. In the first half of the year the hackers' median dwell time dropped to five days from nine in 2022.

Two vulnerabilities affecting some version of Jupiter X Core, a premium plugin for setting up WordPress and WooCommerce websites, allow hijacking accounts and uploading files without authentication. Jupiter X Core is an easy-to-use yet powerful visual editor, part of the Jupiter X theme, which is used in over 172,000 websites.

The North Korean state-backed hacker group tracked as Lazarus has been exploiting a critical vulnerability in Zoho's ManageEngine ServiceDesk to compromise an internet backbone infrastructure provider and healthcare organizations. Cisco Talos researchers observed attacks against UK internet firms in early 2023, when Lazarus leveraged an exploit for CVE-2022-47966, a pre-authentication remote code execution flaw affecting multiple Zoho ManageEngine products.