Security News

Hackers are massively exploiting a remote code execution vulnerability, CVE-2021-25094, in the Tatsu Builder plugin for WordPress, which is installed on about 100,000 websites. Tatsu Builder is a popular plugin that offers powerful template editing features integrated right into the web browser.

The U.S. Cybersecurity and Infrastructure Security Agency on Monday added two security flaws, including the recently disclosed remote code execution bug affecting Zyxel firewalls, to its Known Exploited Vulnerabilities Catalog, citing evidence of active exploitation. Tracked as CVE-2022-30525, the vulnerability is rated 9.8 for severity and relates to a command injection flaw in select versions of the Zyxel firewall that could enable an unauthenticated adversary to execute arbitrary commands on the underlying operating system.

A 28-year-old Ukrainian national has been sentenced to four years in prison for siphoning thousands of server login credentials and selling them on the dark web for monetary gain as part of a credential theft scheme. The illegal sale involved the trafficking of login credentials to servers located across the world and personally identifiable information such as dates of birth and Social Security numbers belonging to U.S. residents on a darknet marketplace.

It's a no-brainer then that data security should be at the center of your overall security strategy. That means being able to detect and neutralize threats, ensure data is protected even when bad actors make it through, and being able to remediate and restore your data quickly if the worst does happen.

Hackers have started to exploit a recently patched critical vulnerability, tracked as CVE-2022-30525, that affects Zyxel firewall and VPN devices for businesses. It is unclear if these efforts are malicious or just researchers working to map up Zyxel devices currently exposed to adversary attacks.

A ransomware group with an Iranian operational connection has been linked to a string of file-encrypting malware attacks targeting organizations in Israel, the U.S., Europe, and Australia. Cybersecurity firm Secureworks attributed the intrusions to a threat actor it tracks under the moniker Cobalt Mirage, which it said is linked to an Iranian hacking crew dubbed Cobalt Illusion.

Threat analysts have spotted a novel attack attributed to the Iranian hacking group known as APT34 group or Oilrig, who targeted a Jordanian diplomat with custom-crafted tools. The attack involved advanced anti-detection and anti-analysis techniques and had some characteristics that indicate lengthy and careful preparation.
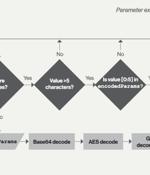
NET-based post-exploitation framework called IceApple that has been deployed on Microsoft Exchange server instances to facilitate reconnaissance and data exfiltration. "Suspected to be the work of a state-nexus adversary, IceApple remains under active development, with 18 modules observed in use across a number of enterprise environments, as of May 2022," CrowdStrike said in a Wednesday report.
Many of the victimized entities were U.S.-based financial institutions and brokerage firms that suffered direct system compromise from Mustapha and his co-conspirators, who performed unauthorized transactions using other peoples' brokerage accounts. "The defendant was part of a nefarious group that caused millions of dollars in losses to victims by engaging in a litany of cybercrimes, including widespread hacking, fraud, taking control of victims' securities brokerage accounts, and trading in the name of the victims," stated U.S. Attorney Breon Peace.

An espionage-focused threat actor known for targeting China, Pakistan, and Saudi Arabia has expanded to set its sights on Bangladeshi government organizations as part of an ongoing campaign that commenced in August 2021. Cybersecurity firm Cisco Talos attributed the activity with moderate confidence to a hacking group dubbed the Bitter APT based on overlaps in the command-and-control infrastructure with that of prior campaigns mounted by the same actor.