Security News
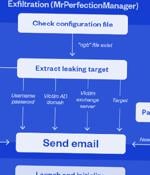
The Iranian nation-state hacking group known as OilRig has continued to target government organizations in the Middle East as part of a cyber espionage campaign that leverages a new backdoor to exfiltrate data. "The campaign abuses legitimate but compromised email accounts to send stolen data to external mail accounts controlled by the attackers," Trend Micro researchers Mohamed Fahmy, Sherif Magdy, and Mahmoud Zohdy said.

Security researchers warn that hackers may start using Microsoft Visual Studio Tools for Office more often as method to achieve persistence and execute code on a target machine via malicious Office add-ins. NET-based malware and embedding it into the Office add-in.

A new cyber espionage campaign dubbed 'No Pineapple!' has been attributed to the North Korean Lazarus hacking group, allowing the threat actors to stealthily steal 100GB of data from the victim without causing any destruction. The campaign is named after the '' error seen transmitted by a remote access malware when uploading stolen data to the threat actor's servers.

Teams of hackers defend their own computers while attacking other teams'. It's a controlled setting for what computer hackers do in real life: finding and fixing vulnerabilities in their own systems and exploiting them in others'.

A new intelligence gathering campaign linked to the prolific North Korean state-sponsored Lazarus Group leveraged known security flaws in unpatched Zimbra devices to compromise victim systems. Targets of the malicious operation included a healthcare research organization in India, the chemical engineering department of a leading research university, as well as a manufacturer of technology used in the energy, research, defense, and healthcare sectors, suggesting an attempt to breach the supply chain.

Google Fi, Google's U.S.-only telecommunications and mobile internet service, has informed customers that personal data was exposed by a data breach at one of its primary network providers, with some customers warned that it allowed SIM swapping attacks. Google sent notices of a data breach to Google Fi customers this week, informing them that the incident exposed their phone numbers, SIM card serial numbers, account status, account activation date, and mobile service plan details.

Hackers have been targeting online gaming and gambling companies with what appears to be a previously unseen backdoor that researchers have named IceBreaker. Researchers at incident response firm Security Joes believe that the IceBreaker backdoor is a the work of a new advanced threat actor that uses "a very specific social engineering technique," which could lead to a more clear picture of who they are.
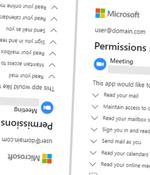
Microsoft on Tuesday said it took steps to disable fake Microsoft Partner Network accounts that were used for creating malicious OAuth applications as part of a malicious campaign designed to breach organizations' cloud environments and steal email.On top of that, Microsoft said it implemented additional security measures to improve the vetting process associated with the Microsoft Cloud Partner Program and minimize the potential for fraud in the future.

GitHub on Monday disclosed that unknown threat actors managed to exfiltrate encrypted code signing certificates pertaining to some versions of GitHub Desktop for Mac and Atom apps. The Microsoft-owned subsidiary said it detected unauthorized access to a set of deprecated repositories used in the planning and development of GitHub Desktop and Atom on December 7, 2022.

QNAP is warning customers to install QTS and QuTS firmware updates that fix a critical security vulnerability allowing remote attackers to inject malicious code on QNAP NAS devices. "A vulnerability has been reported to affect QNAP devices running QTS 5.0.1 and QuTS hero h5.0.1. If exploited, this vulnerability allows remote attackers to inject malicious code,' warns the QNAP security advisory."