Security News

The maintainers of the PyTorch package have warned users who have installed the nightly builds of the library between December 25, 2022, and December 30, 2022, to uninstall and download the latest versions following a dependency confusion attack. "PyTorch-nightly Linux packages installed via pip during that time installed a dependency, torchtriton, which was compromised on the Python Package Index code repository and ran a malicious binary," the PyTorch team said in an alert over the weekend.

Software development isn't only about code; more importantly, it's driven by a set of best practices and guidelines that help us write better and more secure software. Like all large software companies, Microsoft has developed its own set of policies and procedures to implement approaches like its Secure Software Development Lifecycle.
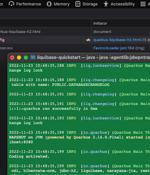
A critical security vulnerability has been disclosed in the Quarkus Java framework that could be potentially exploited to achieve remote code execution on affected systems. "The vulnerability is found in the Dev UI Config Editor, which is vulnerable to drive-by localhost attacks that could lead to remote-code execution," Contrast Security researcher Joseph Beeton, who reported the bug, said in a write-up.
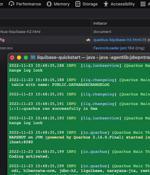
A critical security vulnerability has been disclosed in the Quarkus Java framework that could be potentially exploited to achieve remote code execution on affected systems. "The vulnerability is found in the Dev UI Config Editor, which is vulnerable to drive-by localhost attacks that could lead to remote-code execution," Contrast Security researcher Joseph Beeton, who reported the bug, said in a write-up.

Google's Threat Analysis Group has linked an exploit framework that targets now-patched vulnerabilities in the Chrome and Firefox web browsers and the Microsoft Defender security app to a Spanish software company. While TAG is Google's team of security experts focused on protecting Google users from state-sponsored attacks, it also keeps track of dozens of companies that enable governments to spy on dissidents, journalists, and political opponents using surveillance tools.

New Alchimist attack framework hits Windows, Linux and Mac. During initialization, all its content is placed in hard coded folders, namely /tmp/Res for the web interface, HTML files and more folders, and /tmp/Res/Payload for its payloads for Windows and Linux operating systems.

A previously undocumented command-and-control framework dubbed Alchimist is likely being used in the wild to target Windows, macOS, and Linux systems. "Alchimist C2 has a web interface written in Simplified Chinese and can generate a configured payload, establish remote sessions, deploy payload to the remote machines, capture screenshots, perform remote shellcode execution, and run arbitrary commands," Cisco Talos said in a report shared with The Hacker News.

Cybersecurity researchers have discovered a new attack and C2 framework called 'Alchimist,' which appears to be actively used in attacks targeting Windows, Linux, and macOS systems. Alchimist offers a web-based interface using the Simplified Chinese language, and it's very similar to Manjusaka, a recently-emerged post-exploitation attack framework growing popular among Chinese hackers.
A game changer in cyber incident response, the Dissect framework enables data acquisition on thousands of systems within hours, regardless of the nature and size of the IT environment to be investigated after an attack. Now it is available on GitHub to the security community as open source software to help advance and accelerate forensic data collection and analysis.

A months-long cyber espionage campaign undertaken by a Chinese nation-state group targeted several entities with reconnaissance malware so as to glean information about its victims and meet its strategic goals. "The targets of this recent campaign spanned Australia, Malaysia, and Europe, as well as entities that operate in the South China Sea," enterprise security firm Proofpoint said in a published in partnership with PwC. Targets encompass local and federal Australian Governmental agencies, Australian news media companies, and global heavy industry manufacturers which conduct maintenance of fleets of wind turbines in the South China Sea.