Security News

A member of U.S. Navy's red team has published a tool called TeamsPhisher that leverages an unresolved security issue in Microsoft Teams to bypass restrictions for incoming files from users outside of a targeted organization, the so-called external tenants. The tool exploits a problem highlighted last month by Max Corbridge and Tom Ellson of UK-based security services company Jumpsec, who explained how an attacker could easily go around Microsoft Teams' file-sending restraints to deliver malware from an external account.

Hackers exploit a zero-day privilege escalation vulnerability in the 'Ultimate Member' WordPress plugin to compromise websites by bypassing security measures and registering rogue administrator accounts. Ultimate Member is a user profile and membership plugin that facilitates sign-ups and building communities on WordPress sites, and it currently has over 200,000 active installations.

Data protection vendor Arcserve has addressed a high-severity security flaw in its Unified Data Protection backup software that can let attackers bypass authentication and gain admin privileges.According to the company, Arcserve UDP is a data and ransomware protection solution designed to help customers thwart ransomware attacks, restore compromised data, and enable effective disaster recovery to ensure business continuity.

Proof-of-concept exploit code for the high-severity vulnerability in Cisco Secure Client Software for Windows and Cisco AnyConnect Secure Mobility Client Software for Windows has been published. Cisco Secure Client Software - previously known as Cisco AnyConnect Secure Mobility Client - is unified endpoint security software designed to assist businesses in expanding their network access capabilities and enabling remote employees to connect via both wired and wireless connections, including VPN. In early June, Cisco published a security advisory about CVE-2023-20178, a vulnerability in the client update process of both Cisco AnyConnect Secure Mobility Client Software for Windows and Cisco Secure Client Software for Windows.

Proof-of-concept exploit code is now available for a high-severity flaw in Cisco Secure Client Software for Windows that can let attackers elevate privileges to SYSTEM. Cisco Secure Client helps employees to work from anywhere using a secure Virtual Private Network and provides network admins with telemetry and endpoint management features.Cisco released security updates to address this security bug last Tuesday when it said its Product Security Incident Response Team did not have evidence of malicious use or public exploit code targeting the bug in the wild.

The North Korean threat actor known as ScarCruft has been observed using an information-stealing malware with previous undocumented wiretapping features as well as a backdoor developed using Golang that exploits the Ably real-time messaging service. "The threat actor sent their commands through the Golang backdoor that is using the Ably service," the AhnLab Security Emergency response Center said in a technical report.

Progress Software on Friday issued a fix for a third critical bug in its MOVEit file transfer suite, a vulnerability that had just been disclosed the day earlier. A researcher who goes by the handle MCKSys Argentina confirmed to The Register that a June 16 MOVEit patch for CVE-2023-35708 mitigated the researcher's PoC exploit code, which was shared in screenshot form.
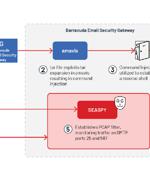
A suspected China-nexus threat actor dubbed UNC4841 has been linked to the exploitation of a recently patched zero-day flaw in Barracuda Email Security Gateway appliances since October 2022. "UNC4841 is an espionage actor behind this wide-ranging campaign in support of the People's Republic of China," Google-owned Mandiant said in a new report published today, describing the group as "Aggressive and skilled."

In what's a new kind of software supply chain attack aimed at open source projects, it has emerged that threat actors could seize control of expired Amazon S3 buckets to serve rogue binaries without altering the modules themselves. "Malicious binaries steal the user IDs, passwords, local machine environment variables, and local host name, and then exfiltrates the stolen data to the hijacked bucket," Checkmarx researcher Guy Nachshon said.

The Chinese state-sponsored group known as UNC3886 has been found to exploit a zero-day flaw in VMware ESXi hosts to backdoor Windows and Linux systems. The VMware Tools authentication bypass vulnerability, tracked as CVE-2023-20867, "Enabled the execution of privileged commands across Windows, Linux, and PhotonOS guest VMs without authentication of guest credentials from a compromised ESXi host and no default logging on guest VMs," Mandiant said.