Security News
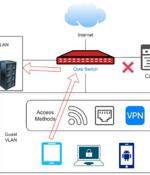
Cybersecurity researchers have detailed as many as five severe security flaws in the implementation of TLS protocol in several models of Aruba and Avaya network switches that could be abused to gain remote access to enterprise networks and steal valuable information. The new set of flaws, dubbed TLStorm 2.0, renders Aruba and Avaya network switches vulnerable to remote code execution vulnerabilities, enabling an adversary to commandeer the devices, move laterally across the network, and exfiltrate sensitive data.

Five critical remote code execution vulnerabilities in millions Aruba and Avaya devices can be exploited by cybercriminals to take full control of network switches commonly used in airports, hospitals, and hotels, according to Armis researchers. The flaws affect about 10 million devices across HPE's Aruba and Extreme Networks' Avaya switching portfolio, and have severity scores ranging from 9.0 to 9.8 out of 10.

Russia's invasion on Ukraine has put a spotlight on threats to critical infrastructure, which thus far have been mostly physical, impacting water treatment, electricity, and nuclear plants. These threats to critical infrastructure may seem distant, but the involvement of the FBI shows they are not.

Users of Synology and QNAP network-attached storage devices are advised to be on the lookout for patches for several critical vulnerabilities affecting Netatalk, an open-source implemention of the Apple Filing Protocol that allows Unix-like operating systems to serve file servers for Macs.Network-attached storage devices are usually used by small-to-medium businesses and home users for storing and sharing files and backups.

Synology has warned customers that some of its network-attached storage appliances are exposed to attacks exploiting multiple critical Netatalk vulnerabilities. "Multiple vulnerabilities allow remote attackers to obtain sensitive information and possibly execute arbitrary code via a susceptible version of Synology DiskStation Manager and Synology Router Manager," Synology said.

Taiwanese corporation QNAP has asked customers this week to disable the AFP file service protocol on their network-attached storage appliances until it fixes multiple critical Netatalk vulnerabilities. On QNAP NAS devices, AFP allows macOS systems to access data on the NAS. According to QNAP, it's still used because it "Supports many unique macOS attributes that are not supported by other protocols."

Advanced hackers are actively exploiting a critical remote code execution vulnerability, CVE-2022-22954, that affects in VMware Workspace ONE Access.The issue was addressed in a security update 20 days ago along with two more RCEs - CVE-2022-22957 and CVE-2022-22958 that also affect VMware Identity Manager, VMware vRealize Automation, VMware Cloud Foundation, and vRealize Suite Lifecycle Manager.
A security vulnerability has been disclosed in the web version of the Ever Surf wallet that, if successfully weaponized, could allow an attacker to gain full control over a victim's wallet. "In other words, attackers could gain full control over the victim's wallets."

Atlassian has published a security advisory warning of a critical vulnerability in its Jira software that could be abused by a remote, unauthenticated attacker to circumvent authentication protections. Tracked as CVE-2022-0540, the flaw is rated 9.9 out of 10 on the CVSS scoring system and resides in Jira's authentication framework, Jira Seraph.

Atlassian has published a security advisory to alert that its Jira and Jira Service Management products are affected by a critical authentication bypass vulnerability in Seraph, the company's web application security framework.Seraph is used in Jira and Confluence for handling all login and logout requests via a system of pluggable core elements.