Security News

The Shadowserver Foundation fulfills a unique role in the cybersecurity ecosystem by supplying vital security information to Internet defenders and law enforcement at no cost. In this Help Net Security video, Piotr Kijewski, CEO at The Shadowserver Foundation, talks about what they do and offers insight into their track record of delivering high-quality, actionable cyber threat intelligence for over 15 years.

Researchers have disclosed details about a now-patched critical flaw in the Move virtual machine that powers the Aptos blockchain network. The vulnerability "Can cause Aptos nodes to crash and cause denial of service," Singapore-based Numen Cyber Labs said in a technical write-up published earlier this month.

Security researchers observed malicious campaigns leveraging a critical vulnerability in VMware Workspace One Access to deliver various malware, including the RAR1Ransom tool that locks files in password-protected archives. Researchers at cybersecurity company Fortinet noticed in the newest campaigns that the threat actors deployed the Mira botnet for distributed denial-of-service attacks, the GuardMiner cryptocurrency miner, and the RAR1Ransom tool.

WordPress security company Wordfence on Thursday said it started detecting exploitation attempts targeting the newly disclosed flaw in Apache Commons Text on October 18, 2022. While the issue was originally reported in early March 2022, the Apache Software Foundation released an updated version of the software on September 24, followed by issuing an advisory only last week on October 13.

The U.S. Cybersecurity and Infrastructure Security Agency on Tuesday released two Industrial Control Systems advisories pertaining to severe flaws in Advantech R-SeeNet and Hitachi Energy APM Edge appliances.Patches have been made available in version R-SeeNet version 2.4.21 released on September 30, 2022.
HelpSystems, the company behind the Cobalt Strike software platform, has released an out-of-band security update to address a remote code execution vulnerability that could allow an attacker to take control of targeted systems. Cobalt Strike is a commercial red-team framework that's mainly used for adversary simulation, but cracked versions of the software have been actively abused by ransomware operators and espionage-focused advanced persistent threat groups alike.

While knowing full well that human lives may be at stake, criminal gangs have been increasingly targeting the healthcare sector with high-impact attacks like ransomware. Healthcare providers should set up numerous layers of defense for a variety of email-borne threats.

We hear the term data sovereignty more and more these days. That's strange in some ways because the rules for flinging data around the world have been a challenge for decades - particularly since the internet hit critical mass in the late 1990s and early 2000s and international data transfers went from being a rarity to the norm.
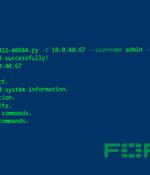
A proof-of-concept exploit code has been made available for the recently disclosed critical security flaw affecting Fortinet FortiOS, FortiProxy, and FortiSwitchManager, making it imperative that users move quickly to apply the patches. "FortiOS exposes a management web portal that allows a user to configure the system," Horizon3.

Proof-of-concept exploit code is now available for a critical authentication bypass vulnerability affecting Fortinet's FortiOS, FortiProxy, and FortiSwitchManager appliances.Ai security researchers released a proof-of-concept exploit and a technical root cause analysis for this vulnerability today, following an announcement that a CVE-2022-40684 PoC will be made available this week.