Security News

Check Point found attackers could transmit a specially designed radio packet to a nearby device to crash the firmware, ending that equipment's cellular connectivity, at least, presumably until it's rebooted. UNISOC is a 21-year-old chip designer based in China that spent the first 17 years of life known as Spreadtrum Communications, and that by 2011 was supplying chips for more than half of the mobile phones in the country.

A Chinese-speaking hacking group known as LuoYu is infecting victims WinDealer information stealer malware deployed by switching legitimate app updates with malicious payloads in man-on-the-side attacks. LuoYu has switched to abusing the automatic update mechanism of their victims' apps after previously pushing malware in easier to pull-off watering-hole attacks where they would use compromised local news sites as infection vectors.

An advanced persistent threat actor aligned with Chinese state interests has been observed weaponizing the new zero-day flaw in Microsoft Office to achieve code execution on affected systems. "TA413 CN APT spotted exploiting the Follina zero-day using URLs to deliver ZIP archives which contain Word Documents that use the technique," enterprise security firm Proofpoint said in a tweet.

Chinese-linked threat actors are now actively exploiting a Microsoft Office zero-day vulnerability to execute malicious code remotely on Windows systems. This Microsoft Windows Support Diagnostic Tool remote code execution flaw impacts all Windows client and server platforms still receiving security updates.

A researcher from the Beijing Institute of Tracking and Telecommunications advocated for Chinese military capability to take out Starlink satellites on the grounds of national security in a peer-reviewed domestic journal. According to the South China Morning Post, lead author Ren Yuanzhen and colleagues advocated in Modern Defence Technology not only for China to develop anti-satellite capabilities, but also to have a surveillance system that could monitor and track all satellites in Starlink's constellation.

Trend Micro says it patched a DLL hijacking flaw in Trend Micro Security used by a Chinese threat group to side-load malicious DLLs and deploy malware. As Sentinel Labs revealed in an early-May report, the attackers exploited the fact that security products run with high privileges on Windows to plant and load their own maliciously crafted DLL into memory, allowing them to elevate privileges and execute code.
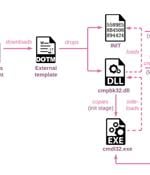
At least two research institutes located in Russia and a third likely target in Belarus have been at the receiving end of an espionage attack by a Chinese nation-state advanced persistent threat. The attacks, codenamed "Twisted Panda," come in the backdrop of Russia's military invasion of Ukraine, prompting a wide range of threat actors to swiftly adapt their campaigns on the ongoing conflict to distribute malware and stage opportunistic attacks.

Microsoft search engine Bing censors terms deemed sensitive in China from its autosuggestion feature internationally, according to research from Citizen Lab. The University of Toronto research organization analyzed the search engine's autosuggestion system for censorship of nearly 100,000 names in the United States, Canada and China in both English letters and Chinese characters.

A previously unknown Chinese hacking group known as 'Space Pirates' targets enterprises in the Russian aerospace industry with phishing emails to install novel malware on their systems. Russian threat analysts at Positive Technologies named the group "Space Pirates" due to their espionage operations focusing on stealing confidential information from companies in the aerospace field.

To predict the targets of new Chinese malware, keep an eye on new Chinese government policies, a threat intelligence analyst suggested at the Black Hat Asia conference on Thursday. Yew later told The Register the attacks against foreign gambling firms might also be attempts to collect data for the crackdown campaigns.