Security News

The zero-day exploitation of a now-patched medium-security flaw in the Fortinet FortiOS operating system has been linked to a suspected Chinese hacking group. Threat intelligence firm Mandiant, which made the attribution, said the activity cluster is part of a broader campaign designed to deploy backdoors onto Fortinet and VMware solutions and maintain persistent access to victim environments.

Meet the newest member of the crypto rogues' gallery: Ho Wan Kwok, aka Guo Wengui, aka Miles Guo, whom the US Department of Justice on Wednesday arrested over what investigators have described as a "Sprawling and complex scheme to solicit investments in various entities and programs through false statements and representations to hundreds of thousands of Kwok's online followers." One of Guo's operations was called Himalaya Exchange.

Suspected Chinese spies have exploited a critical Fortinet bug, and used custom networking malware to steal credentials and maintain network access, according to Mandiant security researchers. "Mandiant suspected the FortiGate and FortiManager devices were compromised due to the connections to VIRTUALPITA from the Fortinet management IP addresses," the researchers observed.

A suspected Chinese hacking group has been linked to a series of attacks on government organizations exploiting a Fortinet zero-day vulnerability to deploy malware. The security flaw allowed threat actors to deploy malware payloads by executing unauthorized code or commands on unpatched FortiGate firewall devices, as Fortinet disclosed last week.

Threat activity clusters affiliated with the Chinese and Russian cybercriminal ecosystems have been observed using a new piece of malware that's designed to load Cobalt Strike onto infected machines. The development comes as improved detection capabilities against Cobalt Strike, a legitimate post-exploitation tool used for red team operations, is forcing threat actors to seek alternative options or concoct new ways to propagate the framework to evade detection.

Chinese squid fishing boats are overwhelming Ecuador and Peru. As usual, you can also use this squid post to talk about the security stories in the news that I haven't covered.

Suspected Chinese cyber criminals have zeroed in on unpatched SonicWall gateways and are infecting the devices with credential-stealing malware that persists through firmware upgrades, according to Mandiant. The spyware targets the SonicWall Secure Mobile Access 100 Series - a gateway device that provides VPN access to remote users.
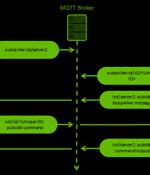
The China-aligned Mustang Panda actor has been observed using a hitherto unseen custom backdoor called MQsTTang as part of an ongoing social engineering campaign that commenced in January 2023. "Unlike most of the group's malware, MQsTTang doesn't seem to be based on existing families or publicly available projects," ESET researcher Alexandre Côté Cyr said in a new report.

The Chinese cyber espionage hacking group Mustang Panda was seen deploying a new custom backdoor named 'MQsTTang' in attacks starting this year. Mustang Panda is an advanced persistent threat group known to target organizations worldwide in data theft attacks using customized versions of the PlugX malware.

Microsoft on Monday attributed a China-based cyber espionage actor to a set of attacks targeting diplomatic entities in South America. The threat actor is said to use established hacking tools such as ShadowPad to infiltrate targets and maintain persistent access.