Security News

Infosec outfit Checkpoint says it's spotted a Chinese actor targeting diplomatic facilities around Europe. Checkpoint has dubbed the campaign "SmugX" thanks to its use of HTML smuggling to deploy the PlugX remote access trojan.

A Chinese nation-state group has been observed targeting Foreign Affairs ministries and embassies in Europe using HTML smuggling techniques to deliver the PlugX remote access trojan on compromised systems. "The campaign uses new delivery methods to deploy a new variant of PlugX, an implant commonly associated with a wide variety of Chinese threat actors," Check Point said.

What is new is the extent to which the balloon was driven by US hardware, which unnamed sources told the Wall Street Journal was "Crammed" with off-the-shelf components that could have easily been purchased online. In February, US officials added six Chinese companies to its trade-restricting Entity List over their work with the Chinese government to develop high-altitude balloons like the one in question.

The newly discovered Chinese nation-state actor known as Volt Typhoon has been observed to be active in the wild since at least mid-2020, with the hacking crew linked to never-before-seen tradecraft to retain remote access to targets of interest. "The adversary consistently employed ManageEngine Self-service Plus exploits to gain initial access, followed by custom web shells for persistent access, and living-off-the-land techniques for lateral movement," the cybersecurity company said.

Malware intended to spread on USB drives is unintentionally infecting networked storage devices, according to infosec vendor Checkpoint. "Upon returning to his home hospital in Europe, the employee introduced the infected USB drive to the hospital's computer systems, which led the infection to spread.".

Foreign affairs ministries in the Americas have been targeted by a Chinese state-sponsored actor named Flea as part of a recent campaign that spanned from late 2022 to early 2023. The cyber attacks, per Broadcom's Symantec, involved a new backdoor codenamed Graphican.

The Chinese state-sponsored hacking group tracked as APT15 has been observed using a novel backdoor named 'Graphican' in a new campaign between late 2022 and early 2023. APT15, also known as Nickel, Flea, Ke3Chang, and Vixen Panda, are Chinese state hackers targeting important public and private organizations worldwide since at least 2004.

European commissioner Thierry Breton wants Huawei and ZTE barred throughout the EU, and revealed plans to remove kit made by the Chinese telecom vendors from the Commission's internal networks. There are concerns that backdoors in Huawei equipment could allow China to spy on foreign nations, given Chinese law requires local businesses to share info with Beijing.

Chinese spies are behind the data-stealing malware injected into Barracuda's Email Security Gateway devices globally as far back as October 2022, according to Mandiant. Mandiant, who has been working with Barracuda to investigate the exploit used and the malware subsequently deployed, today identified a China-based threat group it tracks as UNC4841, and said the snoops targeted a "Subset" of Barracuda ESG appliances across several regions and sectors.
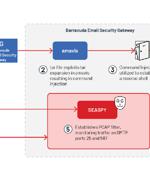
A suspected China-nexus threat actor dubbed UNC4841 has been linked to the exploitation of a recently patched zero-day flaw in Barracuda Email Security Gateway appliances since October 2022. "UNC4841 is an espionage actor behind this wide-ranging campaign in support of the People's Republic of China," Google-owned Mandiant said in a new report published today, describing the group as "Aggressive and skilled."