Security News

Cybersecurity researchers have disclosed details of an artificial intelligence (AI) powered platform called AkiraBot that's used to spam website chats, comment sections, and contact forms to...
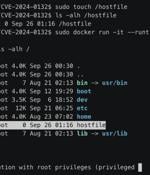
Cybersecurity researchers have discovered a bypass for a now-patched security vulnerability in the NVIDIA Container Toolkit that could be exploited to break out of a container's isolation...
Attackers are increasingly turning to session hijacking to get around widespread MFA adoption. The data supports this, as: 147,000 token replay attacks were detected by Microsoft in 2023, a 111%...

The financially motivated threat actor known as FIN7 has been observed using multiple pseudonyms across several underground forums to likely advertise a tool known to be used by ransomware groups like Black Basta. "AvNeutralizer, a highly specialized tool developed by FIN7 to tamper with security solutions, has been marketed in the criminal underground and used by multiple ransomware groups," cybersecurity company SentinelOne said in a report shared with The Hacker News.

Cybercriminals have been increasingly using a new phishing-as-a-service platform named 'Tycoon 2FA' to target Microsoft 365 and Gmail accounts and bypass two-factor authentication protection. Tycoon 2FA attacks involve a multi-step process where the threat actor steals session cookies by using a reverse proxy server hosting the phishing web page, which intercepts the victim's input and relays them to the legitimate service.

Best EDR Of The Market is a user-mode endpoint detection and response project designed to serve as a testing ground for understanding and bypassing EDR's user-mode detection methods. These techniques are mainly based on a dynamic analysis of the target process state,.

Apple has joined the rapidly growing chorus of tech organizations calling on British lawmakers to revise the nation's Online Safety Bill - which for now is in the hands of the House of Lords - so that it safeguards strong end-to-end encryption. "It also helps everyday citizens defend themselves from surveillance, identity theft, fraud, and data breaches. The Online Safety Bill poses a serious threat to this protection, and could put UK citizens at greater risk."

Thieves cut through the wall of a coffee shop to get to an Apple store, bypassing the alarms in the process. My favorite example is a band of California art thieves that would break into people's houses by cutting a hole in their walls with a chainsaw.
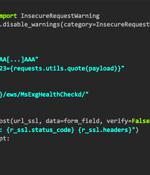
The threat group tracked as REF2924 has been observed deploying previously unseen malware in its attacks aimed at entities in South and Southeast Asia. The malware, dubbed NAPLISTENER by Elastic Security Labs, is an HTTP listener programmed in C# and is designed to evade "Network-based forms of detection."

Signal is urging its global community to help people in Iran stay connected with each other and the rest of the world by volunteering proxies to bypass the aggressive restrictions imposed by the Iranian regime. On Monday, the Iranian regime severely restricted internet connectivity in the country, imposing broad blocks on all ISPs, sometimes leaving internet users entirely offline for several hours.