Security News

This Mark of the Web is an alternate data stream that contains information about the file, such as the URL security zone the file originates from, its referrer, and its download URL. When a user attempts to open a file with a MoTW attribute, Windows will display a security warning asking if they are sure they wish to open the file. After analyzing the files, Will Dormann, a senior vulnerability analyst at ANALYGENCE, discovered that the threat actors were using a new Windows zero-day vulnerability that prevented Mark of the Web security warnings from being displayed.

Cybersecurity researcher David Schütz accidentally found a way to bypass the lock screen on his fully patched Google Pixel 6 and Pixel 5 smartphones, enabling anyone with physical access to the device to unlock it. Exploiting the vulnerability to bypass the lock screen on Android phones is a simple five-step process that wouldn't take more than a few minutes.

According to Schütz, he stumbled on a total Android lockscreen bypass bug entirely by accident in June 2022, under real-life conditions that could easily have happened to anyone. In Schütz's case, it was the humble PIN on his SIM card that stumped him, and because SIM PINs can be as short as four digits, they're protected by a hardware lockout that limits you to three guesses at most.
Google has resolved a high-severity security issue affecting all Pixel smartphones that could be trivially exploited to unlock the devices. "The issue allowed an attacker with physical access to bypass the lock screen protections and gain complete access to the user's device," Schütz, who was awarded $70,000 for the lock screen bypass, said in a write-up of the flaw.

VMware has released security updates to address three critical severity vulnerabilities in the Workspace ONE Assist solution that enable remote attackers to bypass authentication and elevate privileges to admin. Workspace ONE Assist provides remote control, screen sharing, file system management, and remote command execution to help desk and IT staff remotely access and troubleshoot devices in real time from the Workspace ONE console.

Citrix is urging customers to install security updates for a critical authentication bypass vulnerability in Citrix ADC and Citrix Gateway."Note that only appliances that are operating as a Gateway are affected by the first issue, which is rated as a Critical severity vulnerability," explains the Citrix security bulletin.

A new Windows zero-day allows threat actors to use malicious stand-alone JavaScript files to bypass Mark-of-the-Web security warnings. Windows includes a security feature called Mark-of-the-Web that flags a file as having been downloaded from the Internet and should be treated with caution as it could be malicious.

A free unofficial patch has been released through the 0patch platform to address an actively exploited zero-day flaw in the Windows Mark of the Web security mechanism. Windows automatically adds MotW flags to all documents and executables downloaded from untrusted sources, including files extracted from downloaded ZIP archives, using a special 'Zone.Id' alternate data stream.
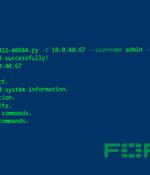
A proof-of-concept exploit code has been made available for the recently disclosed critical security flaw affecting Fortinet FortiOS, FortiProxy, and FortiSwitchManager, making it imperative that users move quickly to apply the patches. "FortiOS exposes a management web portal that allows a user to configure the system," Horizon3.

Proof-of-concept exploit code is now available for a critical authentication bypass vulnerability affecting Fortinet's FortiOS, FortiProxy, and FortiSwitchManager appliances.Ai security researchers released a proof-of-concept exploit and a technical root cause analysis for this vulnerability today, following an announcement that a CVE-2022-40684 PoC will be made available this week.