Security News
Cybersecurity researchers have discovered an updated version of an Android banking malware called Chameleon that has expanded its targeting to include users in the U.K. and Italy. "Representing a...

IBM Security has dissected some JavaScript code that was injected into people's online banking pages to steal their login credentials, saying 50,000 user sessions with more than 40 banks worldwide were compromised by the malicious software in 2023. This injected code executes on the page in the browser, and intercepts the victim's credentials as they are entered, which can be passed to fraudsters to exploit to drain accounts.

A new malware campaign that emerged in March 2023 used JavaScript web injections to try to steal the banking data of over 50,000 users of 40 banks in North America, South America, Europe, and Japan. Once the victim visits the attackers' compromised or malicious sites, the malware injects a new script tag with a source attribute pointing to an externally hosted script.

This year has seen the emergence of ten new Android banking malware families, which collectively target 985 bank and fintech/trading apps from financial institutes across 61 countries. Banking trojans are malware that targets people's online bank accounts and money by stealing credentials and session cookies, bypassing 2FA protections, and sometimes even performing transactions automatically.
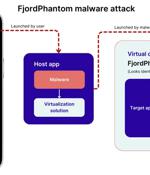
Cybersecurity researchers have disclosed a new sophisticated Android malware called FjordPhantom that has been observed targeting users in Southeast Asian countries like Indonesia, Thailand, and...

63% of respondents indicated that they are comfortable with AI helping their bank detect fraud. Almost half of respondents abandoned a new bank account application after starting because it didn't feel secure or was too cumbersome.

The ACCC has given the green light for cross-banking collaboration to address scams. 1.5 billion came from investment scams, with remote access scams and payment redirection scams rounding out the top three.

Singapore-based infosec outfit Group-IB on Thursday released details of a new Android trojan that exploits the operating system's accessibility features to steal info that enables theft of personal information. The security research outfit wrote that the trojan, named GoldDigger, currently targets Vietnamese banking apps - but includes code suggesting its developers plan wider attacks.
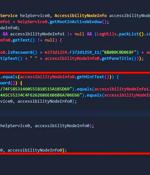
A new Android banking trojan named GoldDigger has been found targeting several financial applications with an aim to siphon victims' funds and backdoor infected devices. "The malware targets more...

An emerging Android banking trojan called Zanubis is now masquerading as a Peruvian government app to trick unsuspecting users into installing the malware. "Zanubis's main infection path is...