Security News

Users of Monzo, one of the UK's most popular digital-only banking platforms, are being targeted by phishing messages supported by a growing network of malicious websites. Monzo is a 100% online banking platform with over four million customers and among the first to challenge the traditional financial managing system.

Open banking APIs handle everything from account status to fund transfers to pin changes and account services. On top of open banking driving API utilization, APIs have become a de facto standard in modern application development, with organizations often deploying thousands of APIs for a wide variety of purposes.
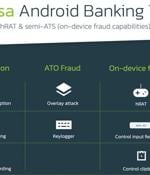
Two different Android banking Trojans, FluBot and Medusa, are relying on the same delivery vehicle as part of a simultaneous attack campaign, according to new research published by ThreatFabric. The ongoing side-by-side infections, facilitated through the same smishing infrastructure, involved the overlapping usage of "App names, package names, and similar icons," the Dutch mobile security firm said.

The app, which is fully functional as a 2FA authenticator, comes loaded with the Vultur stealer malware that targets and swoops down on financial data. Once downloaded, the app installs Vultur banking trojan, which steals financial and banking data on the compromised device - but can do much more.

A financially-motivated malware campaign has compromised over 800 WordPress websites to deliver a banking trojan dubbed Chaes targeting Brazilian customers of Banco do Brasil, Loja Integrada, Mercado Bitcoin, Mercado Livre, and Mercado Pago. "Chaes is characterized by the multiple-stage delivery that utilizes scripting frameworks such as JScript, Python, and NodeJS, binaries written in Delphi, and malicious Google Chrome extensions," Avast researchers Anh Ho and Igor Morgenstern said.

A large-scale campaign involving over 800 compromised WordPress websites is spreading banking trojans that target the credentials of Brazilian e-banking users. Although the security firm notified the Brazilian CERT, the campaign is ongoing, with hundreds of websites still compromised with malicious scripts that push the malware.
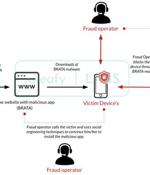
The Android malware tracked as BRATA has been updated with new features that grants it the ability to track device locations and even perform a factory reset in an apparent bid to cover up fraudulent wire transfers. "What makes Android RAT so interesting for attackers is its capability to operate directly on the victim devices instead of using a new device," Cleafy researchers noted in December 2021.
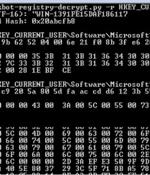
Cybersecurity researchers have decoded the mechanism by which the versatile Qakbot banking trojan handles the insertion of encrypted configuration data into the Windows Registry. Although mainly fashioned as an information-stealing malware, Qakbot has since shifted its goals and acquired new functionality to deliver post-compromise attack platforms such as Cobalt Strike Beacon, with the final objective of loading ransomware on infected machines.

The major players in the space were simply too large to facilitate a quick digital transformation, but the arrival of nimble start-ups and changing user habits have really led them to embrace digital banking. The move to online banking presents a larger attack surface for cybercriminals to exploit and attack.

An ongoing ZLoader malware campaign has been uncovered exploiting remote monitoring tools and Microsoft's digital signature verification to siphon user credentials and sensitive information. "The malware then exploits Microsoft's digital signature verification method to inject its payload into a signed system DLL to further evade the system's defenses."