Security News

A Chinese-speaking threat actor has hacked into the building automation systems of several Asian organizations to backdoor their networks and gain access to more secured areas in their networks. The APT group, whose activity was spotted by Kaspersky ICS CERT researchers, focused on devices unpatched against CVE-2021-26855, one of the Microsoft Exchange vulnerabilities collectively known as ProxyLogon.
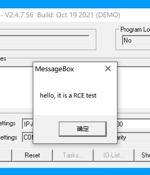
CODESYS has released patches to address as many as 11 security flaws that, if successfully exploited, could result in information disclosure and a denial-of-service condition, among others. CODESYS is a software suite used by automation specialists as a development environment for programmable logic controller applications.

Deepwatch released the State of the Modern SOC report, which found that most IT security professionals believe they could have stopped business impacting cyber events if equipped with better response capabilities. Many seek more automation and less alert noise to shorten response times.
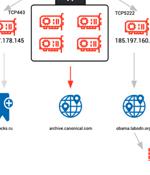
Cybersecurity researchers are calling attention to a free-to-use browser automation framework that's being increasingly used by threat actors as part of their attack campaigns. The U.S. cybersecurity company said it observed command-and-control IP addresses associated with malware such as Bumblebee, BlackGuard, and RedLine Stealer establishing connections to the downloads subdomain of Bablosoft, the maker of the Browser Automation Studio.

Microsoft is rolling out its "Security Experts" managed service with an eye on stomping down threats and malware. Microsoft is planning to roll out three such managed services in 2022, one of which became available today.
Chris Hass, director of information security and research at Automox, discusses how the future looks. While the trend of automation will continue to grow, there still remain many challenges to its adoption, and new innovations or threats could change how the future looks for this technology.

A team of UTSA researchers is exploring how a new automated approach could prevent software security vulnerabilities. The team sought to develop a deep learning model that could teach software how to extract security policies automatically.

The proven approach in the market today is with digital certificates, which leverage PKI. In fact, some of the best authentication mechanisms leverage digital certificates at their core. In this case, when leveraging digital certificates as a baseline for human and machine identities, digital certificates must be provisioned to users and devices, and ultimately, orchestrated and automated.

The challenge faced by already strained IT teams is how to deliver strong certificate management across increasingly complex IT environments, at a time when workforces are massively distributed and entering the corporate network via the consumer-grade technologies in their homes. While third-party certificate authorities are a trusted option for many enterprises across the globe, many choose instead to issue them in-house, operating their own "Private CAs" to fulfill at least a portion of their PKI needs.

The research finds that investments in automation are directly linked to increased business revenues, job growth, and long-term productivity. Automation investments boost revenue and economic resilience.