Security News

Juniper Networks has released security updates to address a critical security flaw impacting Session Smart Router, Session Smart Conductor, and WAN Assurance Router products that could be...

Hackers are launching attacks against Palo Alto Networks PAN-OS firewalls by exploiting a recently fixed vulnerability (CVE-2025-0108) that allows bypassing authentication. [...]

Palo Alto Networks has fixed a high-severity authentication bypass vulnerability (CVE-2025-0108) in the management web interface of its next-gen firewalls, a proof-of-concept exploit (PoC) for...

Palo Alto Networks has addressed a high-severity security flaw in its PAN-OS software that could result in an authentication bypass. The vulnerability, tracked as CVE-2025-0108, carries a CVSS...

Here’s an easy system for two humans to remotely authenticate to each other, so they can be sure that neither are digital impersonations. To mitigate that risk, I have developed this simple...

You can easily add a fingerprint reader to your computer if one isn't already built in.

Learn how to protect yourself and your sensitive information from phishing attacks by implementing multi-factor authentication.

APIs have emerged as the predominant attack surface over the past year, with AI being the biggest driver of API security risks, according to Wallarm. “Based on our findings, what is clear is that...

As a company fortunate enough to have and maintain our own pentesting team, we often do outreach with other organizations to assist with or provide our expertise in offensive security. In...
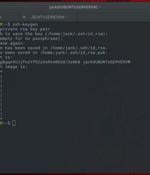
Here's how to use the secure copy command, in conjunction with ssh key authentication, for an even more secure means of copying files to your remote Linux servers.