Security News
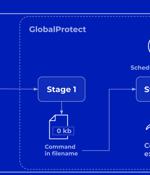
Palo Alto Networks has shared more details of a critical security flaw impacting PAN-OS that has come under active exploitation in the wild by malicious actors. The company described the...

Users of the CrushFTP enterprise file transfer software are being urged to update to the latest version following the discovery of a security flaw that has come under targeted exploitation in the...

Dutch chipmaker Nexperia confirmed late last week that hackers breached its network in March 2024 after a ransomware gang leaked samples of allegedly stolen data. Ransomware gang starts leaking alleged stolen Change Healthcare data.

The United Nations Development Programme is investigating a cyberattack after threat actors breached its IT systems to steal human resources data. While the UN agency has yet to link the attack to a specific threat group, the 8Base ransomware gang added a new UNDP entry to its dark web data leak website on March 27.

Approximately 22,500 exposed Palo Alto GlobalProtect firewall devices are likely vulnerable to the CVE-2024-3400 flaw, a critical command injection vulnerability that has been actively exploited in attacks since at least March 26, 2024. CVE-2024-3400 is a critical vulnerability impacting specific Palo Alto Networks' PAN-OS versions in the GlobalProtect feature that allows unauthenticated attackers to execute commands with root privileges using command injection triggered by arbitrary file creation.

In an ongoing Kubernetes cryptomining campaign, attackers target OpenMetadata workloads using critical remote code execution and authentication vulnerabilities. The security vulnerabilities exploited in these attacks were patched one month ago, on March 15, in OpenMedata versions 1.2.4 and 1.3.1.

The financially motivated threat actor FIN7 targeted a large U.S. car maker with spear-phishing emails for employees in the IT department to infect systems with the Anunak backdoor. BlackBerry attributed the attacks to FIN7 with a high level of confidence based on the use of unique PowerShell scripts using the adversary's signature 'PowerTrash' obfuscated shellcode invoker, first seen in a 2022 campaign.

A previously undocumented "flexible" backdoor called Kapeka has been "sporadically" observed in cyber attacks targeting Eastern Europe, including Estonia and Ukraine, since at least mid-2022. The...

While it initially seemed that protecting Palo Alto Network firewalls from attacks leveraging CVE-2024-3400 would be possible by disabling the devices' telemetry, it has now been comfirmed that this mitigation is ineffectual."Device telemetry does not need to be enabled for PAN-OS firewalls to be exposed to attacks related to this vulnerability," Palo Alto Networks noted on Tuesday, and said they are aware of an "Increasing number of attacks that leverage the exploitation of this vulnerability."

Cisco is warning about a global surge in brute-force attacks targeting various devices, including Virtual Private Network (VPN) services, web application authentication interfaces, and SSH...