Security News

Palo Alto firewalls: Public exploits, rising attacks, ineffective mitigationWhile it initially seemed that protecting Palo Alto Network firewalls from attacks leveraging CVE-2024-3400 would be possible by disabling the devices' telemetry, it has now been confirmed that this mitigation is ineffectual. Geopolitical tensions escalate OT cyber attacksIn this Help Net Security interview, Andrew Ginter, VP of Industrial Security at Waterfall Security, discusses operational technology cyber attacks and their 2024 Threat Report.

While it initially seemed that protecting Palo Alto Network firewalls from attacks leveraging CVE-2024-3400 would be possible by disabling the devices' telemetry, it has now been comfirmed that this mitigation is ineffectual."Device telemetry does not need to be enabled for PAN-OS firewalls to be exposed to attacks related to this vulnerability," Palo Alto Networks noted on Tuesday, and said they are aware of an "Increasing number of attacks that leverage the exploitation of this vulnerability."

This quick glossary, created by Mark W. Kaelin for TechRepublic Premium, explains the terminology used by security experts as they attempt to reduce the damage caused by a successful attack. Evidence may include documents, logs, software or hardware.

Basically, DLP systems are aimed at prevention of data leaks, and in real-life mode they monitor and block transmitting of confidential data. That's why SearchInform offers the next-gen platform for internal threat mitigation - Risk Monitor.

Ivanti warned admins to stop pushing new device configurations to appliances after applying mitigations because this will leave them vulnerable to ongoing attacks exploiting two zero-day vulnerabilities. "Customers should stop pushing configurations to appliances with the XML in place, and not resume pushing configurations until the appliance is patched," Ivanti said in a new update published on Saturday.

The U.S. Department of Justice (DOJ) and the FBI recently collaborated in a multinational operation to dismantle the notorious Qakbot malware and botnet. While the operation was successful in...

The rise of Generative-AI apps and GPT services exacerbates this issue, with employees of all departments rapidly adding the latest and greatest AI apps to their productivity arsenal, without the security team's knowledge. From engineering apps such as code review and optimization to marketing, design and sales apps such as content & video creation, image creation and email automation apps.

Even if you're not a MOVEit customer, and even if you'd never heard of the MOVEit file sharing software before the end of last month. As you can imagine, because this security hole existed in the web front-end to the MOVEit software, and because MOVEit is all about uploading, sharing and downloading corporate files with ease, these criminals abused the bug to grab hold of trophy data to give themselves blackmail leverage over their victims.

The top challenges when implementing an effective cyber/IT risk management program include an increase in the quantity and severity of cyber threats, a lack of funding and a lack of staffing/cyber risk talent. Given the financial and reputational consequences of cyberattacks, corporate board rooms are putting pressure on CISOs to identify and mitigate cyber/IT risk.
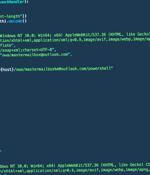
Threat actors affiliated with a ransomware strain known as Play are leveraging a never-before-seen exploit chain that bypasses blocking rules for ProxyNotShell flaws in Microsoft Exchange Server to achieve remote code execution through Outlook Web Access. "The new exploit method bypasses URL rewrite mitigations for the Autodiscover endpoint," CrowdStrike researchers Brian Pitchford, Erik Iker, and Nicolas Zilio said in a technical write-up published Tuesday.