Security News
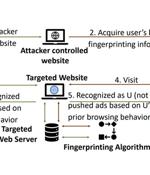
A "Potentially devastating and hard-to-detect threat" could be abused by attackers to collect users' browser fingerprinting information with the goal of spoofing the victims without their knowledge, thus effectively compromising their privacy. Academics from Texas A&M University dubbed the attack system "Gummy Browsers," likening it to a nearly 20-year-old "Gummy Fingers" technique that can impersonate a user's fingerprint biometrics.

Historically, it's a big national security concern, as it should be, whether other governments might be poison-pilling some of our software and supply chains. CW. Well, certainly one place to start with as a software provider is understanding that the security of your software is only as good as the security of your entire environment that's used to build and maintain that software.

Russia's Nobelium group - fingered as being a Russian state actor by both the United States and Britain - has massively ramped up phishing and password spraying attempts against managed service providers and cloud resellers, Microsoft's security arm has warned. The Windows maker said the group's targeted attacks against "Resellers and other technology service providers that customize, deploy and manage cloud services and other technologies on behalf of their customers" had trebled over the past three months.

The UK's largest retailer, supermarket titan Tesco, has restored its online operations after an attack hack left its customers unable to order, amend, or cancel deliveries for two days. A Tesco statement acknowledges disruption to the giant's grocery website and app, claiming "An attempt was made to interfere with our systems, which has caused problems with the search function on the site."

The state of bot mitigation 64% of organizations lost more than 6% of their revenue due to bot attacks, and 32% lost 10% or more within the last year. 64% of organizations lost 6% or more of their revenue due to bot attacks, and 32% report that their organizations lost 10% or more of revenue within the last 12 months.

Microsoft on Thursday disclosed an "Extensive series of credential phishing campaigns" that takes advantage of a custom phishing kit that stitched together components from at least five different widely circulated ones with the goal of siphoning user login information. Phishing kits, often sold as one time payments in underground forums, are packaged archive files containing images, scripts, and HTML pages that enable a threat actor to set up phishing emails and pages, using them as lures to harvest and transmit credentials to an attacker-controlled server.

The financially motivated FIN7 cybercrime gang has masqueraded as yet another fictitious cybersecurity company called "Bastion Secure" to recruit unwitting software engineers under the guise of penetration testing in a likely lead-up to a ransomware scheme. "With FIN7's latest fake company, the criminal group leveraged true, publicly available information from various legitimate cybersecurity companies to create a thin veil of legitimacy around Bastion Secure," Recorded Future's Gemini Advisory unit said in a report.

It's not the first time FIN7 has masqueraded as a legitimate security firm, but this latest gambit showcases its continued expansion into the ransomware area, researchers noted. It added that with willing accomplices, FIN7 would be forced to share a percentage of ransom payments - but "FIN7's fake company scheme enables the operators of FIN7 to obtain the talent that the group needs to carry out its criminal activities, while simultaneously retaining a larger share of the profits."

The Groove ransomware gang is calling on other extortion groups to attack US interests after law enforcement took down REvil's infrastructure last week. Yesterday, Reuters reported that REvil's takedown resulted from an international law enforcement operation that included support from the FBI. Today, the Groove ransomware gang published a Russian blog post calling on all other ransomware operations to target US interests.

The Italian data protection authority Garante per la Protezione dei Dati Personali has announced an investigation into a data breach of the country's copyright protection agency. Yesterday, the GPDP announced that they are investigating whether hackers stole the personal data of registered members and employees of SIAE during a ransomware attack.