Security News

Now according to Cisco Talos, advanced persistent threat actors and commodity malware families alike are increasingly using Excel add-in files as an initial intrusion vector. One such method turns out to be XLL files, which is described by Microsoft as a "Type of dynamic link library file that can only be opened by Excel."

BlueNoroff, a subcluster of the notorious Lazarus Group, has been observed adopting new techniques into its playbook that enable it to bypass Windows Mark of the Web protections. "BlueNoroff created numerous fake domains impersonating venture capital companies and banks," security researcher Seongsu Park said, adding the new attack procedure was flagged in its telemetry in September 2022.
Advanced persistent threats are a type of attack that's usually carried out or sponsored by a nation-state, and unlike other types of malware attacks, these pose their own challenges. Typically, an APT threat actor will perform some kind of reconnaissance on their target, and then target their victim by sending, for example, a spear-phishing email.

The report includes evidence of malicious activity linked to ransomware and nation-state backed advanced persistent threat actors. Q3 cybersecurity trends US ransomware activity leads the pack: In the US alone, ransomware activity increased 100% quarter over quarter in transportation and shipping.
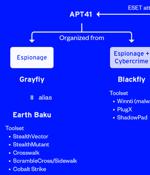
The victimology patterns and the targeted sectors overlap with attacks mounted by a distinct sister group of APT41 known as Earth Baku, the Japanese cybersecurity company added. Some of Earth Baku's malicious cyber activities have been tied to groups called by other cybersecurity firms ESET and Symantec under the names SparklingGoblin and Grayfly, respectively.

A French-speaking threat actor dubbed OPERA1ER has been linked to a series of more than 30 successful cyber attacks aimed at banks, financial services, and telecom companies across Africa, Asia, and Latin America between 2018 and 2022. According to Singapore-headquartered cybersecurity company Group-IB, the attacks have led to thefts totaling $11 million, with actual damages estimated to be as high as $30 million.
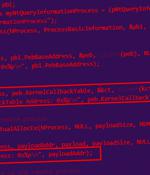
SideWinder, a prolific nation-state actor mainly known for targeting Pakistan military entities, compromised the official website of the National Electric Power Regulatory Authority to deliver a tailored malware called WarHawk. "The newly discovered WarHawk backdoor contains various malicious modules that deliver Cobalt Strike, incorporating new TTPs such as KernelCallBackTable injection and Pakistan Standard Time zone check in order to ensure a victorious campaign," Zscaler ThreatLabz said.
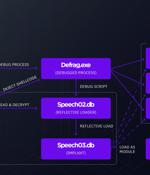
The cybersecurity firm codenamed the group Metador in reference to a string "I am meta" in one of their malware samples and because of Spanish-language responses from the command-and-control servers. The threat actor is said to have primarily focused on the development of cross-platform malware in its pursuit of espionage aims.

A Linux variant of a backdoor known as SideWalk was used to target a Hong Kong university in February 2021, underscoring the cross-platform abilities of the implant. In August 2021, ESET unearthed a new piece of custom Windows malware codenamed SideWalk that was exclusively leveraged by the actor to strike an unnamed computer retail company based in the U.S. Subsequent findings from Symantec, part of Broadcom software, have linked the use of SideWalk to an espionage attack group it tracks under the moniker Grayfly, while pointing out the malware's similarities to that of Crosswalk.

North Korean APT Lazarus is up to its old tricks with a cyberespionage campaign targeting engineers with a fake job posting that attempt to spread macOS malware. The malware is similar to a sample discovered by ESET in May, which also included a signed executable disguised as a job description, was compiled for both Apple and Intel, and dropped a PDF decoy, researchers said.