Security News > 2022 > November > New "Earth Longzhi" APT Targets Ukraine and Asian Countries with Custom Cobalt Strike Loaders
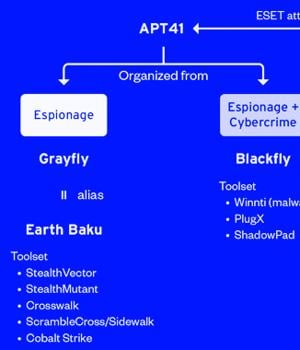
The victimology patterns and the targeted sectors overlap with attacks mounted by a distinct sister group of APT41 known as Earth Baku, the Japanese cybersecurity company added.
Some of Earth Baku's malicious cyber activities have been tied to groups called by other cybersecurity firms ESET and Symantec under the names SparklingGoblin and Grayfly, respectively.
Now Earth Longzhi adds to another piece in the APT41 attack puzzle, what with the actor also sharing links to a third subgroup dubbed GroupCC. Attacks orchestrated by the hacker group leverage spear-phishing emails as the initial entry vector.
These messages are known to embed password-protected archives or links to files hosted on Google Drive that, when opened, launches a Cobalt Strike loader dubbed CroxLoader.
In some cases, the group has been observed weaponizing remote code execution flaws in publicly exposed applications to deliver a web shell capable of dropping a next-stage loader referred to as Symatic that's engineered to deploy Cobalt Strike.
The second series of attacks initiated by Earth Longzhi follow a similar pattern, the main difference being the use of different Cobalt Strike loaders named CroxLoader, BigpipeLoader, and OutLoader to drop the red team framework on infected hosts.
News URL
https://thehackernews.com/2022/11/new-earth-longzhi-apt-targets-ukraine.html