Security News

Uncommon TTPs. With time, money and other resources on their side, APTs such as Cozy Bear, OceanLotus, and Grim Spider conduct technically intricate, cutting-edge attacks that potentially threaten any organization. It's a tactic that allows APTs to gain access to the target organization through the users' systems without directly attacking them.

An APT group linked to Russia’s Foreign Intelligence Service has hit employees of several dozen global organizations with phishing attacks via Microsoft Teams, says Microsoft. A social engineering...

Turla has been targeting defense sector organizations in Ukraine and Eastern Europe with DeliveryCheck and Kazuar backdoors / infostealers and has been using compromised Microsoft Exchange servers to control them. Turla APT. Turla is a sophisticated and persistent APT group that has been active for over 10 years and is believed to be sponsored by the Russian state.

US-based enterprise software firm JumpCloud says a state-backed hacking group breached its systems almost one month ago as part of a highly targeted attack focused on a limited set of customers.On July 5, JumpCloud discovered "Unusual activity in the commands framework for a small set of customers" while investigating the attack and analyzing logs for signs of malicious activity in collaboration with IR partners and law enforcement.

Rockwell Automation says a new remote code execution exploit linked to an unnamed Advanced Persistent Threat group could be used to target unpatched ControlLogix communications modules commonly used in manufacturing, electric, oil and gas, and liquified natural gas industries.The company teamed up with the U.S. Cybersecurity and Infrastructure Security Agency to analyze the exploit linked to APT threat actors, but they have yet to share how they obtained it.

Rockwell Automation has fixed two vulnerabilities in the communication modules of its ControlLogix industrial programmable logic controllers, ahead of expected in-the-wild exploitation. "An unreleased exploit capability leveraging these vulnerabilities is associated with an unnamed APT group," industrial cybersecurity company Dragos has stated on Wednesday.

By analyzing a year's worth of APT campaign data they collected from the 200,000+ SMBs that have their security solution deployed, they pinpointed three main trends of attacks targeting SMBs in the space of a year. SMBs often lack adequate cybersecurity measures, making them vulnerable to all kinds of cyber threats.
The threat actor known as Dark Pink has been linked to five new attacks aimed at various entities in Belgium, Brunei, Indonesia, Thailand, and Vietnam between February 2022 and April 2023. Dark Pink, also called Saaiwc Group, is an advanced persistent threat actor believed to be of Asia-Pacific origin, with attacks targeting entities primarily located in East Asia and, to a lesser extent, in Europe.
A previously undetected advanced persistent threat actor dubbed Red Stinger has been linked to attacks targeting Eastern Europe since 2020. Red Stinger overlaps with a threat cluster Kaspersky revealed under the name Bad Magic last month as having targeted government, agriculture, and transportation organizations located in Donetsk, Lugansk, and Crimea last year.

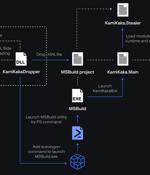
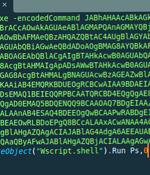
An advanced persistent threat actor known as Dragon Breath has been observed adding new layers of complexity to its attacks by adopting a novel DLL side-loading mechanism. "The attack is based on a classic side-loading attack, consisting of a clean application, a malicious loader, and an encrypted payload, with various modifications made to these components over time," Sophos researcher Gabor Szappanos said.