Security News

CVE-2024-43461, a spoofing vulnerability affecting Windows MSHTML – a software component used by various apps for rendering render web pages on Windows – “was exploited as a part of an attack...

Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: SonicWall patches critical flaw affecting its firewalls (CVE-2024-40766) SonicWall has patched a...
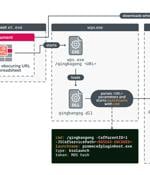
A South Korea-aligned cyber espionage has been linked to the zero-day exploitation of a now-patched critical remote code execution flaw in Kingsoft WPS Office to deploy a bespoke backdoor dubbed...

ESET researchers discovered a remote code execution vulnerability in WPS Office for Windows (CVE-2024-7262). APT-C-60, a South Korea-aligned cyberespionage group, was exploiting it to target East...

The zero-day exploit used to leverage CVE-2024-38112, a recently patched Windows MSHTML vulnerability, was wielded by an APT group dubbed Void Banshee to deliver malware to targets in North America, Europe, and Southeast Asia, threat hunters with Trend Micro's Zero Day Initiative have shared. As previously explained by Check Point researcher Haifei Li, the attackers used files that were specially crafted to exploit the vulnerability but were made to look like PDFs. "The threat actor leveraged CVE-2024-38112 to execute malicious code by abusing the MHTML protocol handler and x-usc directives through internet shortcut files. Using this technique, the threat actor was able to access and run files directly through the disabled Internet Explorer instance on Windows machines," Trend Micro researchers noted.

An advanced persistent threat group called Void Banshee has been observed exploiting a recently disclosed security flaw in the Microsoft MHTML browser engine as a zero-day to deliver an information stealer called Atlantida. "Variations of the Atlantida campaign have been highly active throughout 2024 and have evolved to use CVE-2024-38112 as part of Void Banshee infection chains," security researchers Peter Girnus and Aliakbar Zahravi said.

The SEXi ransomware operation, known for targeting VMware ESXi servers, has rebranded under the name APT INC and has targeted numerous organizations in recent attacks. The ransomware operation was given the name SEXi based on the SEXi.txt ransom note name and the.

A previously undocumented advanced persistent threat group dubbed CloudSorcerer has been observed targeting Russian government entities by leveraging cloud services for command-and-control and data exfiltration. "It's a sophisticated cyber espionage tool used for stealth monitoring, data collection, and exfiltration via Microsoft Graph, Yandex Cloud, and Dropbox cloud infrastructure," the Russian security vendor said.

The remote access software company TeamViewer is warning that its corporate environment was breached in a cyberattack yesterday, with a cybersecurity firm claiming it was by an APT hacking group. "On Wednesday, 26 June 2024, our security team detected an irregularity in TeamViewer's internal corporate IT environment," TeamViewer said in a post to its Trust Center.

Governmental entities in the Middle East, Africa, and Asia are the target of a Chinese advanced persistent threat (APT) group as part of an ongoing cyber espionage campaign dubbed Operation...