Security News

Apple has released patches for three zero-day vulnerabilities exploited in the wild. Referencing Kaspersky's findings, Apple says that those last two vulnerabilities "May have been actively exploited against versions of iOS released before iOS 15.7.".

Apple on Wednesday released a slew of updates for iOS, iPadOS, macOS, watchOS, and Safari browser to address a set of flaws it said were actively exploited in the wild. The iPhone maker said it's aware that the two issues "May have been actively exploited against versions of iOS released before iOS 15.7," crediting Kaspersky researchers Georgy Kucherin, Leonid Bezvershenko, and Boris Larin for reporting them.

Whoever is infecting people's iPhones with the TriangleDB spyware may be targeting macOS computers with similar malware, according to Kaspersky researchers. In the security shop's ongoing analysis of the smartphone snooping campaign - during which attackers exploit a kernel vulnerability to obtain root privileges and install TriangleDB on victims' handsets - Kaspersky analysts uncovered 24 commands provided by the malware that can be used for a range of illicit activities; everything from stealing data, to tracking the victim's geolocation, and terminating processes.

Apple addressed three new zero-day vulnerabilities exploited in attacks installing Triangulation spyware on iPhones via iMessage zero-click exploits. The attacks started in 2019 and are still ongoing, according to Kaspersky, who reported in early June that some iPhones on its network were infected with previously unknown spyware via iMessage zero-click exploits that exploited iOS zero-day bugs.

Cybersecurity researchers have uncovered a set of malicious artifacts that they say is part of a sophisticated toolkit targeting Apple macOS systems. On devices running macOS, Base64-encoded content retrieved from the server is written to a file named "/Users/Shared/AppleAccount.
Apple is introducing major updates to Safari Private Browsing, offering users better protections against third-party trackers as they browse the web. "Advanced tracking and fingerprinting protections go even further to help prevent websites from using the latest techniques to track or identify a user's device," the iPhone maker said.

On the positive side, Apple hosted its annual Worldwide Developers Conference this week with announcements around the new Vision Pro 'spatial computer' powered by the new visionOS, iOS 17 updates, the upcoming Sonoma OS release, new M2 hardware, and much more. On the negative side, in mid-May Apple released zero-day updates to address three critical vulnerabilities.

Apple announced on Monday at WWDC 2023 its much anticipated Vision Pro augmented reality device, which CEO Tim Cook promised would be a revolutionary advance. During the keynote, Apple also announced iOS 17, macOS 14 Sonoma, iPadOS 17, new Apple Watch features and an array of hardware upgrades.

Russian intelligence has accused American snoops and Apple of working together to backdoor iPhones to spy on "Thousands" of diplomats worldwide. A Kaspersky spokesperson told The Register it's aware of the FSB claims, but can't say if the two things - Uncle Sam backdooring iPhones, and the spyware found on several Kaspersky devices - are linked.
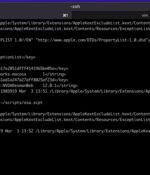
Microsoft has shared details of a now-patched flaw in Apple macOS that could be abused by threat actors with root access to bypass security enforcements and perform arbitrary actions on affected devices. "The most straight-forward implication of a SIP bypass is that an attacker can create files that are protected by SIP and therefore undeletable by ordinary means," Microsoft researchers Jonathan Bar Or, Michael Pearse, and Anurag Bohra said.