Security News > 2024 > May

Can I change location without a VPN? The main question many users have is whether they need a VPN service to change their location. To change your VPN location and IP again, simply connect to another country in your VPN app.

Since the first edition of The Ultimate SaaS Security Posture Management (SSPM) Checklist was released three years ago, the corporate SaaS sprawl has been growing at a double-digit pace. In large...
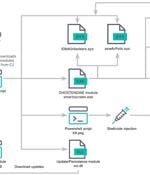
Cybersecurity researchers have discovered a new cryptojacking campaign that employs vulnerable drivers to disable known security solutions (EDRs) and thwart detection in what's called a Bring...

Veeam has patched four vulnerabilities in Backup Enterprise Manager, one of which may allow attackers to bypass authentication and log in to its web interface as any user.Veeam Backup Enterprise Manager is an application that is used to manage the Veeam Backup & Replication solution - a backup/restore app for virtual and physical machines and cloud-based workloads - via a web console.

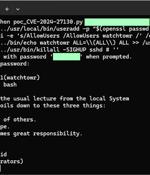
An unknown threat actor is exploiting known security flaws in Microsoft Exchange Server to deploy a keylogger malware in attacks targeting entities in Africa and the Middle East. Russian...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.
Taiwanese company QNAP has rolled out fixes for a set of medium-severity flaws impacting QTS and QuTS hero, some of which could be exploited to achieve code execution on its network-attached...

Popular enterprise services provider Zoom has announced the rollout of post-quantum end-to-end encryption (E2EE) for Zoom Meetings, with support for Zoom Phone and Zoom Rooms coming in the future....

Authelia is an open-source authentication and authorization server that offers 2FA and SSO for applications through a web portal. Authelia connects directly to the reverse proxy but never to the application backends.

In this role, you'll lead biomedical ICT and cybersecurity initiatives, provide training, design solutions, conduct risk assessments, manage security incidents, and ensure compliance. The Information Security Officer is a key role in the IS Governance Security team.