Security News > 2024 > April

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

The MITRE Corporation reported a cyber attack that began in January 2024, involving a nation-state actor exploiting two zero-day vulnerabilities in Ivanti Connect Secure appliances. The attack compromised MITRE's Networked Experimentation, Research, and Virtualization Environment (NERVE), which is an unclassified network used for research and prototyping.The attackers used these vulnerabilities to bypass multi-factor authentication and execute arbitrary commands. They gained initial access, moved laterally within the network, and compromised the VMware infrastructure using an administrator account. This allowed them to deploy backdoors and web shells for ongoing access and data extraction.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Between crossovers - Do threat actors play dirty or desperate? In our dataset of over 11,000 victim organizations that have experienced a Cyber Extortion / Ransomware attack, we noticed that some...
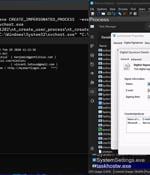
New research has found that the DOS-to-NT path conversion process could be exploited by threat actors to achieve rootkit-like capabilities to conceal and impersonate files, directories, and...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Microsoft has revealed that North Korea-linked state-sponsored cyber actors has begun to use artificial intelligence (AI) to make its operations more effective and efficient. "They are learning to...
In this article, we'll identify some first steps you can take to establish your cloud security strategy. We'll do so by discussing the cloud security impact of individual, concrete actions featured within the CIS Critical Security Controls and the CIS Benchmarks.

In this Help Net Security interview, Roy Davis, Manager - Vulnerability Management & Bug Bounty at Zoom, discusses the role bug bounty programs play in identifying security vulnerabilities and facilitating collaboration with researchers. Disputes over bug classifications: Bug bounty programs usually have guidelines for classifying the severity of reported vulnerabilities, and determining the reward amount.