Security News > 2024 > March

Threat hunters have discovered a set of seven packages on the Python Package Index (PyPI) repository that are designed to steal BIP39 mnemonic phrases used for recovering private keys of a...

A cursory scan of the major ransomware groups' leak blogs shows none of the big names are yet claiming responsibility for the attack on Leicester City Council. "Over the weekend we have continued to work with our cybersecurity and law enforcement partners, as well as learning from other councils who have had attacks, to identify the nature of the incident and the steps we need to take to get our systems back online," said Richard Sword, strategic director of city developments and neighborhoods at Leicester City Council.

About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I've been writing about security issues on my blog since 2004, and in my monthly newsletter since 1998.
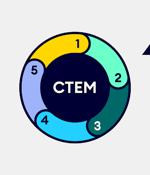
In a world of ever-expanding jargon, adding another FLA (Four-Letter Acronym) to your glossary might seem like the last thing you’d want to do. But if you are looking for ways to continuously...
A new malware campaign is leveraging a high-severity security flaw in the Popup Builder plugin for WordPress to inject malicious JavaScript code. According to Sucuri, the campaign has infected...

A financially motivated threat actor is using known vulnerabilities to target public-facing services and deliver custom malware to unpatched Windows and Linux systems. Magnet Goblin - as the threat actor has been dubbed by Check Point researchers - has been targeting unpatched edge devices and public-facing servers for years.

Russia has detained a South Korean national for the first time on cyber espionage charges and transferred from Vladivostok to Moscow for further investigation. The development was first...

Several French government websites have been disrupted by a severe distributed denial of service attack. A statement from prime minister Gabriel Attal's office acknowledged that some sites were in trouble as of Sunday night, and mentioned conventional attacks of unprecedented intensity.

As cybersecurity professionals, we consider the security risks and implications it presents for businesses, and we must do our best to remain in control and set clear boundaries and limitations on what the technology can do. When we think about the security implications of interactive AI, we must first consider the concerns that have previously been raised around generative AI models and LLMs. These range from ethical concerns to political and ideological biases, uncensored models, and offline functionality.

Reporting directly to the Chief Product and Technology Officer, you will oversee all aspects of information security, including cloud security, DevSecOps, security operations, and security strategy. You'll conduct risk analyses, develop policies, and enhance cybersecurity architecture, making information security a measurable, integral part of our clients' organizations.