Security News > 2024 > January

Cybersecurity researchers have shed light on the command-and-control (C2) server of a known malware family called SystemBC. "SystemBC can be purchased on underground marketplaces and is supplied...

Malicious activity targeting a critical severity flaw in the 'Better Search Replace' WordPress plugin has been detected, with researchers observing thousands of attempts in the past 24 hours. Better Search Replace is a WordPress plugin with more than one million installations that helps with search and replace operations in databases when moving websites to new domains or servers.

US securities lender EquiLend has pulled a number of its systems offline after a security "Incident" in which an attacker gained "Unauthorized access". EquiLend first spotted the attack on January 22 and a statement by the Wall Street staple confirmed there was unauthorized access to part of its infrastructure.

Cozy Bear has been busy hacking and spying on big tech companies: both Microsoft and Hewlett Packard Enterprise have recently disclosed successful attack campaigns by the Russia-affiliated APT group. Last Friday, Microsoft revealed that a threat-actor identified as Midnight Blizzard - a hacking group believed to be associated with the Russian Foreign Intelligence Service - has breached their corporate systems on January 12, 2024.

I am also skeptical that we are going to see useful quantum computers anytime soon. Since at least 2019, I have been saying that this is hard.

The maintainers of the open-source continuous integration/continuous delivery and deployment (CI/CD) automation software Jenkins have resolved nine security flaws, including a critical bug that,...
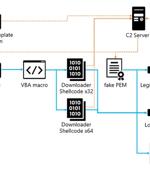
Cybersecurity researchers have uncovered an updated version of a backdoor called LODEINFO that's distributed via spear-phishing attacks. The findings come from Japanese company ITOCHU Cyber &...

The 2023/2024 Axur Threat Landscape Report provides a comprehensive analysis of the latest cyber threats. The information combines data from the platform's surveillance of the Surface, Deep, and...

ESET researchers have discovered NSPX30, a sophisticated implant used by a new China-aligned APT group, which they dubbed Blackwood. It leverages adversary-in-the-middle techniques to hijack update requests from legitimate software to deliver the implant.

All types of cyber threat actor are already using artificial intelligence to varying degrees, UK National Cyber Security Centre's analysts say, and predict that AI "Will almost certainly increase the volume and heighten the impact of cyberattacks over the next two years." Although AI is used by all types of cyber threat actors, it will particularly benefit less-skilled ones, as it will enhance their ability to carry out social engineering attacks and create convincing phishing emails.