Security News > 2023 > September
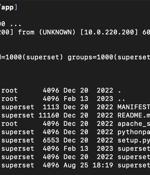
Patches have been released to address two new security vulnerabilities in Apache SuperSet that could be exploited by an attacker to gain remote code execution on affected systems. Outside of these weaknesses, the latest version of Superset also remediates a separate improper REST API permission issue that allows for low-privilege users to carry out server-side request forgery attacks.

Comment Sanity appears to have prevailed in the debate over the UK Online Safety bill after the government agreed to ditch proposals - at least for the time being - to legislate the scanning of encrypted messages. In response to questions regarding the technical feasibility of scanning messages and the assessments that Ofcom must make, Lord Parkinson, a Digital, Culture, Media and Sport minister, said: "If the appropriate technology does not exist that meets these requirements, then Ofcom will not be able to use Clause 122 to require its use."

A Mirai botnet variant called Pandora has been observed infiltrating inexpensive Android-based TV sets and TV boxes and using them as part of a botnet to perform distributed denial-of-service attacks. Doctor Web said the compromises are likely to occur either during malicious firmware updates or when applications for viewing pirated video content are installed.
Microsoft on Wednesday revealed that a China-based threat actor known as Storm-0558 acquired the inactive consumer signing key to forging tokens to access Outlook by compromising an engineer's corporate account. "A consumer signing system crash in April of 2021 resulted in a snapshot of the crashed process," the Microsoft Security Response Center said in a post-mortem report.

LibreOffice is based on the source code of OpenOffice, a project that, according to LibreOffice marketing co-lead Italo Vignoli, was marked by questionable decisions around development and quality assurance. To address the mountain of inherited technical debt, the LibreOffice developers undertook a heavy source code cleanup and refactoring process, which lasted throughout the development of LibreOffice 3.x and 4.x. "This effort was coupled with the creation of an infrastructure to serve the developers, with the implementation of tools such as Gerrit for code review, Git for continuous integration, a battery of Tinderboxes, Bugzilla for quality assurance, OpenGrok for source code research, Weblate for localization, as well as testing for performance and crash analysis," he explained.

Analysis Chinese authorities have reportedly banned Apple's iPhones from some government offices. News of Beijing's ban was reported by the Wall Street Journal, which mentioned people familiar with the matter as having said employees at some central government regulators were told not to use iPhones for work or bring them into the office.

In the context of generative AI, having properly defined user roles to control who can access the AI system, train models, input data, and interpret outputs has become a critical security requirement. You might grant data scientists the authority to train models, while other users might only be permitted to use the model to generate predictions.

Cybercriminals create hundreds of thousands of counterfeit domains that mimic well-known brands for financial gain. These fake domains serve multiple malicious purposes, such as sending phishing emails, hosting fraudulent websites, rerouting web traffic, and distributing malware.

In this Help Net Security interview, Slava Bronfman, CEO at Cybellum, discusses approaches for achieving product security throughout a device's entire lifecycle, fostering collaboration across business units and product lines, ensuring transparency and security in the supply chain, and meeting regulatory requirements while ensuring compliance. The key to ensure a high level of product security in an ever-evolving landscape is to shift both left and right.

The cybersecurity skills crisis continues in a multi-year freefall that has impacted 71% of organizations and left two-thirds of cybersecurity professionals stating that the job has become more difficult over the past two years-while 60% of organizations continue to deflect responsibility, according to a new report from ESG and ISSA. A career in cybersecurity is becoming more difficult in an increasingly challenging environment. The global cybersecurity skills shortage continues unabated.