Security News > 2023 > August

Unpatched Citrix NetScaler systems exposed to the internet are being targeted by unknown threat actors in what's suspected to be a ransomware attack. Attack chains involve the exploitation of CVE-2023-3519, a critical code injection vulnerability impacting NetScaler ADC and Gateway servers that could facilitate unauthenticated remote code execution.
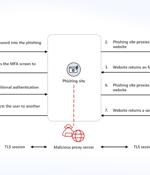
Microsoft is warning of an increase in adversary-in-the-middle phishing techniques, which are being propagated as part of the phishing-as-a-service cybercrime model. In addition to an uptick in AiTM-capable PhaaS platforms, the tech giant noted that existing phishing services like PerSwaysion are incorporating AiTM capabilities.

How does ASM help answer essential questions about the nature and vulnerabilities of an organization's attack surface? Can you provide some insights into the key questions organizations should be asking? ASM should help organizations have a better view of their internet-exposed assets, as well as help them identify the unknown ones.

How many would determine that the best use of their resources would be to attain or retain compliance with a cybersecurity standard? And how many would deploy those compliance and auditing resources to patch more vulnerabilities, invest in additional cybersecurity expertise, tools to identify and reduce their external threat footprint, and myriad other effective measures to genuinely reduce their organization's cyber risk? It's not as if dedication to compliance is any more of a guarantee against a breach than any other technology, strategy or prayer.

DNSdumpster is a free domain research tool that can discover hosts related to a domain. The search works with selectors, i.e. specific search terms such as email addresses, domains, URLs, IPs, CIDRs, Bitcoin addresses, IPFS hashes, etc.

96% of respondents indicated they were still 'confident or very confident' in their organization's SaaS security measures, and yet, 'managing the security of SaaS applications' is the top challenge for IT leaders. The effects of generative AI. IT leaders must now factor the effects of generative AI, such as ChatGPT, into their overall SaaS security approach.

A threat actor believed to be tied to the FIN8 hacking group exploits the CVE-2023-3519 remote code execution flaw to compromise unpatched Citrix NetScaler systems in domain-wide attacks. Resemblances to another attack that Sophos analysts observed earlier in the summer have led the analysts to deduce that the two activities are linked, with the threat actor specializing in ransomware attacks.

Purfoods has notified more than 1.2 million people that their personal and medical data - including payment card and bank account numbers, security codes, and some protected health information - may have been stolen from its servers during what sounds like a ransomware infection earlier this year. According to documents filed with the Maine Attorney General's office and a notification letter mailed to 1,237,681 individuals, criminals broke into Purfoods' network in January 16, encrypted some files containing customer information, and may have stolen others.

Japan's computer emergency response team is sharing a new 'MalDoc in PDF' attack detected in July 2023 that bypasses detection by embedding malicious Word files into PDFs. The file sampled by JPCERT is a polyglot recognized by most scanning engines and tools as a PDF, yet office applications can open it as a regular Word document. The malicious documents in this campaign are a combination of PDF and Word documents, which can be opened as either file format.

Microsoft announced today that Windows Extended Protection will be enabled by default on servers running Exchange Server 2019 starting this fall after installing the 2023 H2 Cumulative Update. Extended Protection is a feature that strengthens Windows Server auth functionality to mitigate authentication relay or "Man in the middle" attacks.