Security News > 2023 > August
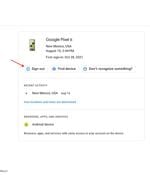
Follow this guide to learn how to easily remove any device from your Google account and keep your account secure. Accessing the Your devices menu from a Google account, you can get an overview of what's connected to your account, find the last location from which a device was used and remove devices - even lost devices - with ease.

Danish cloud hosting firms CloudNordic and Azero - both owned by Certiqa Holding - have suffered a ransomware attack that resulted in most customer data being stolen and systems and servers rendered inaccessible. The companies believe the attack happened while they were transfering servers from one data center to another.

A new study by Critical Insight shows that cybersecurity attacks in the health care sector are hitting more individuals and finding vulnerabilities in third-party partners. A new study by cybersecurity firm Critical Insight noted that while the sheer number of breaches against health care facilities is actually down, there is a spike in the number of people who have been affected by attacks as well as an increase in supply chain and third-party targets.

Recent research suggests that the volume of attacks has doubled in the last year. Experts believe that's in no small part down to the use of generative AI, which is allowing attackers to create more sophisticated and convincing ways to break through security defences.
Dubbed Telekopye, a portmanteau of Telegram and kopye, the toolkit functions as an automated means to create a phishing web page from a premade template and send the URL to potential victims, codenamed Mammoths by the criminals. The attack chains proceed thus: Neanderthals find their Mammoths and try to build rapport with them, before sending a bogus link created using the Telekopye phishing kit via email, SMS, or a direct message.

The North Korean state-backed hacker group tracked as Lazarus has been exploiting a critical vulnerability in Zoho's ManageEngine ServiceDesk to compromise an internet backbone infrastructure provider and healthcare organizations. Cisco Talos researchers observed attacks against UK internet firms in early 2023, when Lazarus leveraged an exploit for CVE-2022-47966, a pre-authentication remote code execution flaw affecting multiple Zoho ManageEngine products.

Public Wi-Fi, which has long since become the norm, poses threats to not only individual users but also businesses. According to the Forbes Advisor the majority of people connect to public Wi-Fi networks that don't require a password.

About Bruce Schneier I am a public-interest technologist, working at the intersection of security, technology, and people. I've been writing about security issues on my blog since 2004, and in my monthly newsletter since 1998.

The SmokeLoader malware is being used to deliver a new Wi-Fi scanning malware strain called Whiffy Recon on compromised Windows machines. "The new malware strain has only one operation. Every 60 seconds it triangulates the infected systems' positions by scanning nearby Wi-Fi access points as a data point for Google's geolocation API," Secureworks Counter Threat Unit said in a statement shared with The Hacker News.
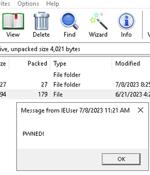
A recently patched security flaw in the popular WinRAR archiving software has been exploited as a zero-day since April 2023, new findings from Group-IB reveal. The vulnerability, cataloged as CVE-2023-38831, allows threat actors to spoof file extensions, thereby making it possible to launch malicious scripts contained within an archive that masquerades as seemingly innocuous image or text files.