Security News > 2023 > July
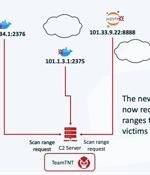
As many as 196 hosts have been infected as part of an aggressive cloud campaign mounted by the TeamTNT group called Silentbob. "The botnet run by TeamTNT has set its sights on Docker and Kubernetes environments, Redis servers, Postgres databases, Hadoop clusters, Tomcat and Nginx servers, Weave Scope, SSH, and Jupyter applications," Aqua security researchers Ofek Itach and Assaf Morag said in a report shared with The Hacker News.

The source code for the BlackLotus UEFI bootkit has leaked online, allowing greater insight into a malware that has caused great concern among the enterprise, governments, and the cybersecurity community. BlackLotus is a Windows-targeting UEFI bootkit that bypasses Secure Boot on fully patched Windows 11 installs, evades security software, persists on an infected system, and executes payloads with the highest level of privileges in the operating system.

The extension enabled threat actors to monitor browser history, take screenshots, and inject malicious scripts that targeted cryptocurrency exchanges. Multiple malicious extensions target user installations, leading to a real danger of data exfiltration and system compromise.

Find out how Google Cloud approaches AI data, what privacy measures your business should keep in mind when it comes to generative AI and how to make a machine learning application "Unlearn" someone's data. Google Cloud approaches using personal data in AI products by covering such data under the existing Google Cloud Platform Agreement.
"In this instance, the PoC is a wolf in sheep's clothing, harboring malicious intent under the guise of a harmless learning tool," Uptycs researchers Nischay Hegde and Siddartha Malladi said. The repository masquerades as a PoC for CVE-2023-35829, a recently disclosed high-severity flaw in the Linux kernel.

Rockwell Automation has fixed two vulnerabilities in the communication modules of its ControlLogix industrial programmable logic controllers, ahead of expected in-the-wild exploitation. "An unreleased exploit capability leveraging these vulnerabilities is associated with an unnamed APT group," industrial cybersecurity company Dragos has stated on Wednesday.

It is taking the novel step of publishing the National Cybersecurity Strategy Implementation Plan to ensure transparency and a continued path for coordination. The Office of the National Cyber Director will coordinate activities under the plan, including an annual report to the President and Congress on the status of implementation, and partner with the Office of Management and Budget to ensure funding proposals in the President's Budget Request are aligned with NCSIP initiatives.

French police should be able to spy on suspects by remotely activating the camera, microphone and GPS of their phones and other devices, lawmakers agreed late on Wednesday, July 5. Covering laptops, cars and other connected objects as well as phones, the measure would allow the geolocation of suspects in crimes punishable by at least five years' jail.

The numerical score can be represented as a qualitative severity rating to help organizations properly assess and prioritize their vulnerability management processes and prepare defences against cyber-attacks.CVSS version 1 was released in February 2005, developed then by a small group of pioneers with the aim of industry-wide adoption, with FIRST appointed that April to drive the future development of what would become a critical tool in the sector's arsenal.

The U.S. Cybersecurity and Infrastructure Security Agency has alerted of two security flaws impacting Rockwell Automation ControlLogix EtherNet/IP communication module models that could be exploited to achieve remote code execution and denial-of-service. "The results and impact of exploiting these vulnerabilities vary depending on the ControlLogix system configuration, but they could lead to denial or loss of control, denial or loss of view, theft of operational data, or manipulation of control for disruptive or destructive consequences on the industrial process for which the ControlLogix system is responsible," Draogos said.