Security News > 2023 > May

A new Android malware distributed as an advertisement SDK has been discovered in multiple apps, many previously on Google Play and collectively downloaded over 400 million times. In the background the trojan SDK checks the Android device's sensor data to confirm that it's not running in a sandboxed environment, commonly used by researchers when analyzing potentially malicious Android apps.

Multiple security flaws uncovered in Sonos One wireless speakers could be potentially exploited to achieve information disclosure and remote code execution, the Zero Day Initiative said in a report published last week. The list of four flaws, which impact Sonos One Speaker 70.3-35220, is below -.

"Because cybercriminals are keen on breaking CAPTCHAs accurately, several services that are primarily geared toward this market demand have been created," Trend Micro said in a report published last week. "These CAPTCHA-solving services don't use techniques or advanced machine learning methods; instead, they break CAPTCHAs by farming out CAPTCHA-breaking tasks to actual human solvers."

A risk-based vulnerability management program is a complex preventative approach used for swiftly detecting and ranking vulnerabilities based on their potential threat to a business. Implementing automation in your vulnerability management is a critical step in maintaining a sound security posture: automation can be used to detect and prioritize threats, apply patches or software upgrades, alert specialists and keep an audit trail - minimizing the time and effort spent, as businesses must act promptly to mitigate the likelihood of exploitation.

Unlike password authentication, which requires a direct match between what is inputted and what's stored in a database, fingerprint authentication determines a match using a reference threshold. As a result, a successful fingerprint brute-force attack requires only that an inputted image provides an acceptable approximation of an image in the fingerprint database.
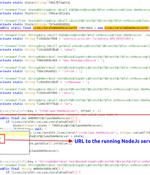
A new open source remote access trojan called DogeRAT targets Android users primarily located in India as part of a sophisticated malware campaign. The malware is distributed via social media and messaging platforms under the guise of legitimate applications like Opera Mini, OpenAI ChatGOT, and Premium versions of YouTube, Netflix, and Instagram.

API calls make up the majority of our digital lives. Take, for example, the everyday use of a cloud-based food delivery app, which could involve up to 25 API calls.

Building a custom cracking rig for research can be expensive, so penetration tester Max Ahartz built one on AWS. In this Help Net Security interview, he takes us through the process and unveils the details of his creation. What motivated you to undertake this project, and what were your objectives in creating the automated cracking rig?

Threat actors are abusing generative AI to carry out child sex abuse material, disinformation, fraud and extremism, according to ActiveFence. Key ways to abuse generative AI:. CSAM. Researchers tracked a 172% increase in the volume of shared CSAM produced by generative AI in the first quarter of this year.

The research shows that cybercriminals continue to barrage organizations with targeted email attacks, and many companies are struggling to keep up. While spear-phishing attacks are low-volume, they are widespread and highly successful compared to other types of email attacks.