Security News > 2023 > May

Webinar A software supply chain attack is a hugely painful form of infiltration which can paralyse any business or organization. An attack like a lethal snake bite where the poison silently and swiftly infects your whole software base.

Improperly deactivated and abandoned Salesforce Sites and Communities could pose severe risks to organizations, leading to unauthorized access to sensitive data. "Because these unused sites are not maintained, they aren't tested against vulnerabilities, and Admins fail to update the site's security measures according to newer guidelines."
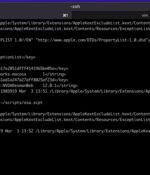
Microsoft has shared details of a now-patched flaw in Apple macOS that could be abused by threat actors with root access to bypass security enforcements and perform arbitrary actions on affected devices. "The most straight-forward implication of a SIP bypass is that an attacker can create files that are protected by SIP and therefore undeletable by ordinary means," Microsoft researchers Jonathan Bar Or, Michael Pearse, and Anurag Bohra said.

Zyxel has patched a high-severity authenticated command injection vulnerability in some of its network attached storage devices aimed at home users. The vulnerability was discovered in the devices' web management interface.

How to do that efficiently and effectively is no small task - but with a small investment of time, you can master threat hunting and save your organization millions of dollars. This article offers a detailed explanation of threat hunting - what it is, how to do it thoroughly and effectively, and how cyber threat intelligence can bolster your threat-hunting efforts.

By analyzing a year's worth of APT campaign data they collected from the 200,000+ SMBs that have their security solution deployed, they pinpointed three main trends of attacks targeting SMBs in the space of a year. SMBs often lack adequate cybersecurity measures, making them vulnerable to all kinds of cyber threats.

Cyber threats are a very real risk, so it's imperative you and your employees know how to keep sensitive company data secure while benefiting from the power of cloud computing. The A to Z Cyber Security & IT Certification Training Bundle will teach you what you need to know about protecting your business's data and operations.

"Human psychology is important to consider from a security team perspective, because we all have cognitive biases," explains Darley. How can AI help us to overcome these cognitive biases? Machine learning can analyse network traffic and identify anomalies or suspicious behaviour that could indicate a cyber attack.
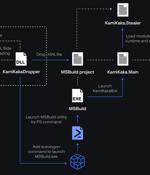
The threat actor known as Dark Pink has been linked to five new attacks aimed at various entities in Belgium, Brunei, Indonesia, Thailand, and Vietnam between February 2022 and April 2023. Dark Pink, also called Saaiwc Group, is an advanced persistent threat actor believed to be of Asia-Pacific origin, with attacks targeting entities primarily located in East Asia and, to a lesser extent, in Europe.

The threat actors behind RomCom RAT are leveraging a network of fake websites advertising rogue versions of popular software at least since July 2022 to infiltrate targets. The remote access trojan has since been used heavily in attacks targeting Ukrainian state bodies and military systems via spoofed versions of legitimate software.