Security News > 2023 > March

Russia's internet watchdog agency Roskomnadzor is warning that today is the first day that laws banning the use of many foreign private messaging applications in the country come into force. The law is "On information, information technology, and information protection," specifically Part 8-10 of Article 10, which prohibits Russian organizations from using information exchange systems owned by foreign entities.

Microsoft has addressed a Windows 11 22H2 known issue causing some apps not to be installed during Windows provisioning. "Using provisioning packages on Windows 11, version 22H2 might not install all expected apps," the company explained in a new update to the Windows Release Health dashboard.

According to the cyber intelligence report from Agari, hybrid phishing attacks have increased by 625%. One of the most damaging is callback phishing - also often known as a TOAD. First appearing in the wild in March 2021 as BazarCall, the attacks were mounted to install ransomware on corporate networks. Low levels of cybersecurity awareness can be the root cause of successful cyberattacks, especially attacks such as Callback phishing.

Attackers can exfiltrate company data stored in Google Cloud Platform storage buckets without leaving obvious forensic traces of the malicious activity in GCP's storage access logs, Mitiga researchers have discovered. "In normal usage, files inside storage objects are read multiple times a day as part of day-to-day activity of the organization," Mitiga cloud incident responder Veronica Marinov noted.

Six different law firms were targeted in January and February 2023 as part of two disparate threat campaigns distributing GootLoader and FakeUpdates malware strains. GootLoader, active since late 2020, is a first-stage downloader that's capable of delivering a wide range of secondary payloads such as Cobalt Strike and ransomware.

A reporter used an AI synthesis of his own voice to fool the voice authentication system for Lloyd’s Bank.

What DNS abuse techniques are employed by cyber adversaries and which organizations can help incident responders and security teams detect, mitigate and prevent them? The DNS Abuse Techniques Matrix published by FIRST provides answers. Among its many special interest groups is the DNS Abuse SIG, which compiled the DNS Abuse Techniques Matrix.
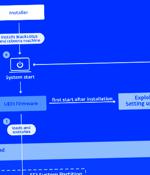
A stealthy Unified Extensible Firmware Interface bootkit called BlackLotus has become the first publicly known malware capable of bypassing Secure Boot defenses, making it a potent threat in the cyber landscape. "This bootkit can run even on fully up-to-date Windows 11 systems with UEFI Secure Boot enabled," Slovak cybersecurity company ESET said in a report shared with The Hacker News.

CISOs at small to midsize businesses with teams of five employees or fewer were surveyed to better understand how work-related stress is impacting CISOs - from their ability to do their job and lead their team to how it's affecting their own professional outlook and personal life. According to the report, 94% of CISOs reported being stressed at work, with 65% confiding that work-stress levels compromised their ability to protect their organizations.

We and our store and/or access information on a device, such as cookies and process personal data, such as unique identifiers and standard information sent by a device for personalised ads and content, ad and content measurement, and audience insights, as well as to develop and improve products. With your permission we and our partners may use precise geolocation data and identification through device scanning.