Security News > 2022 > August

In this Help Net Security video, Christophe Tafani-Dereeper, Cloud Security Researcher and Advocate at DataDog, talks about Stratus Red Team, an open-source project for adversary emulation and validation of threat detection in the cloud. The tool supports common AWS and Kubernetes attack techniques.

Cynerio and the Ponemon Institute have examined the current impact of cyberattacks on healthcare facilities and network-connected IoT and medical devices, and found multiple alarming trends. The Insecurity of Connected Devices in HealthCare 2022 Report surveyed 517 experts in leadership positions at hospitals, clinics, healthcare service providers, and healthcare systems throughout the United States.

Fears over security have become less of a concern for organizations adopting IoT solutions than it was five years ago, according to a recent study by Wi-SUN Alliance, a global member-based association of industry leading companies driving the adoption of interoperable wireless solutions for use in smart cities, smart utilities, IoT and industrial IoT applications. The Journey to IoT Maturity, a follow-up to Wi-SUN's 'state of the nation' IoT study in 2017, is based on interviews with IT decision makers from UK and US IoT adopters within key industries, including energy and utilities, state and local government, construction, technology, and telecommunications.

The report highlights important findings from more than 180 of experienced cybersecurity professionals who reported concerns over attacks against cloud services, ransomware and the growing risks to the global supply chain. An equal number of respondents named vulnerabilities in the systems, applications and networks maintained by contractors, suppliers and customers.

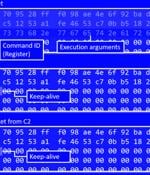
A new social engineering campaign by the notorious North Korean Lazarus hacking group has been discovered, with the hackers impersonating Coinbase to target employees in the fintech industry. A common tactic the hacking group uses is to approach targets over LinkedIn to present a job offer and hold a preliminary discussion as part of a social engineering attack.

Attackers abused open redirects on the websites of Snapchat and American Express in a series of phishing attacks to steal Microsoft 365 credentials. Open redirects are web app weaknesses that allow threat actors to use the domains of trusted organizations and websites as temporary landing pages to simplify phishing attacks.

Browser synchronization abuse: Bookmarks as a covert data exfiltration channelTwo universal and seemingly innocuous browser features - the ability to create bookmarks and browser synchronization - make users' lives easier, but may also allow hackers to establish a covert data exfiltration channel. 6 ways your cloud data security policies are slowing innovation - and how to avoid thatAs practically every organization shifts from managing their data in network-based data centers to storing it in the cloud, cloud data security policies are created to secure this data in a cloud environment.
"This family borrows heavily from the original Mirai source code, but what separates it from other IoT malware families is its built-in capability to brute force credentials and gain access to SSH servers instead of Telnet as implemented in Mirai," Fortinet FortiGuard Labs said in a report. The malware, which gets its name from an embedded URL to a YouTube rap music video in an earlier version, is said to have amassed a growing collection of compromised SSH servers, with over 3,500 unique IP addresses used to scan and brute-force their way into the servers.

A threat actor working to further Iranian goals is said to have been behind a set of disruptive cyberattacks against Albanian government services in mid-July 2022. Cybersecurity firm Mandiant said the malicious activity against a NATO state represented a "Geographic expansion of Iranian disruptive cyber operations."

A late-stage candidate encryption algorithm that was meant to withstand decryption by powerful quantum computers in the future has been trivially cracked by using a computer running Intel Xeon CPU in an hour's time. The algorithm in question is SIKE - short for Supersingular Isogeny Key Encapsulation - which made it to the fourth round of the Post-Quantum Cryptography standardization process by the U.S. Department of Commerce's National Institute of Standards and Technology.