Security News > 2022 > July

Cybersecurity researchers have uncovered new variants of the ChromeLoader information-stealing malware, highlighting its evolving feature set in a short span of time. Primarily used for hijacking victims' browser searches and presenting advertisements, ChromeLoader came to light in January 2022 and has been distributed in the form of ISO or DMG file downloads advertised via QR codes on Twitter and free gaming sites.

The number of UK organizations implementing data encryption as a core part of their cybersecurity strategy has continued to rise, with 32% introducing a policy to encrypt all corporate information as standard in the last year. In total, 47% now require the encryption of all data, whether it's at rest or in transit, according to Apricorn.
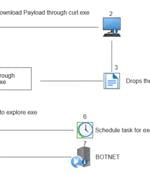
The operators behind the Qakbot malware are transforming their delivery vectors in an attempt to sidestep detection. "Most recently, threat actors have transformed their techniques to evade detection by using ZIP file extensions, enticing file names with common formats, and Excel 4.0 to trick victims into downloading malicious attachments that install Qakbot," Zscaler Threatlabz researchers Tarun Dewan and Aditya Sharma said.

Seasoned fraud expert PJ Rohall has recently become the new Head of Fraud Strategy & Education at SEON. In this Help Net Security interview, he talks about how he entered the industry, about the evolving fraud landscape, and offers advice to other fraud fighters. Do former fraudsters make the best fraud fighters? What attributes do good fraud fighters have in common?
How each side collects the adversary's smartphone location data and shields their own can mean the difference between victory and defeat. Because mobile app location data is often sold to commercial data brokers and then repackaged and sold to individual customers, a country can access such a database and then pick out the phones likely belonging to soldiers.

As an experienced vulnerability management professional and a former system administrator who specialized in patching and remediated 800,000 vulnerabilities over the course of my career, I can offer some realistic perspective on this topic. One reoccurring discussion I've had is how long it takes for a new vulnerability to get exploited.

Cyber resilience is a top priority for global organizations. Understanding threats plays a key role in building and maintaining a strong layered security approach, according to IDC. In this Help Net Security video, Robin Berthier, CEO at Network Perception, talks about strategy for cyber resilience.

Eight months after disclosing a high-severity privilege escalation flaw in vCenter Server's IWA mechanism, VMware has finally released a patch for one of the affected versions. Successful exploitation enables attackers with non-administrative access to unpatched vCenter Server deployments to elevate privileges to a higher privileged group.
Microsoft released its monthly round of Patch Tuesday updates to address 84 new security flaws spanning multiple product categories, counting a zero-day vulnerability that's under active attack in the wild. Very little is known about the nature and scale of the attacks other than an "Exploitation Detected" assessment from Microsoft.

Microsoft has fixed 32 vulnerabilities in the Azure Site Recovery suite that could have allowed attackers to gain elevated privileges or perform remote code execution.The Azure Site Recovery service is a disaster recovery service that will automatically fail-over workloads to secondary locations when a problem is detected.