Security News > 2022 > June

Just employees circumventing regulation using, well, Shadow IT. Not because they tried to obfuscate or hide anything, simply because it was a convenient tool that they preferred over any other sanctioned products. Gartner has identified External Attack Surface Management, Digital Supply Chain Risk, and Identity Threat Detection as the top three trends to focus on in 2022, all of which are closely intertwined with Shadow IT. "Shadow IDs," or in other words, unmanaged employee identities and accounts in third-party services are often created using a simple email-and-password-based registration.
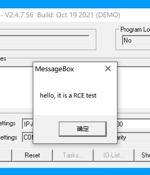
CODESYS has released patches to address as many as 11 security flaws that, if successfully exploited, could result in information disclosure and a denial-of-service condition, among others. CODESYS is a software suite used by automation specialists as a development environment for programmable logic controller applications.

Resecurity, Inc. has identified a spike in phishing content delivered via Azure Front Door, a cloud CDN service provided by Microsoft. According to experts, such tactics confirm how the bad actors are continuously looking to enhance their tactics and procedures to avoid phishing detection using world-known cloud services.

Following the footsteps of Austria and France, the Italian Data Protection Authority has become the latest regulator to find the use of Google Analytics to be non-compliant with E.U. data protection regulations. The agency said the transfer of personal information violates the data protection legislation because the U.S. is a "Country without an adequate level of protection," while highlighting the "Possibility for U.S. government authorities and intelligence agencies to access personal data transferred without due guarantees."

Panther Labs surveyed 400 active security practitioners, primarily, security analysts and security engineers, to reflect the "Boots on the ground" perspective for security teams. Over the last 12 months, 48% have seen a 3x increase in the number of alerts per day.
A malware-as-a-service dubbed Matanbuchus has been observed spreading through phishing campaigns, ultimately dropping the Cobalt Strike post-exploitation framework on compromised machines. "If we look historically, BelialDemon has been involved in the development of malware loaders," Unit 42 researchers Jeff White and Kyle Wilhoit noted in a June 2021 report.

In the same week that it welcomed the launch of a local center of excellence focused on crypto-inspired central bank digital currencies, Singapore's Monetary Authority has warned crypto cowboys they face a rough ride in the island nation. Singapore's sovereign wealth fund has invested in Mojaloop, and MAS chief fintech officer Sopnendu Mohanty serves as a board advisor and the authority provides representatives to the Foundation's working group, alongside folks from the Bill & Melinda Gates Foundation, Google, and more.

Microsoft 365 provides powerful services within Office 365 - but a extensive backup of your Office 365 data is not one of them. Veeam® Backup for Microsoft 365 removes the risk of losing access and control over your Office 365 data, including OneDrive for Business, SharePoint Online, Exchange Online, and Microsoft Teams - so that your data is always protected and accessible.

The beleaguered Israeli surveillanceware vendor NSO Group this week admitted to the European Union lawmakers that its Pegasus tool was used by at least five countries in the region. The disclosure comes as a special inquiry committee was launched in April 2022 to investigate alleged breaches of E.U. law following revelations that the company's Pegasus spyware is being used to snoop on phones belonging to politicians, diplomats, and civil society members.
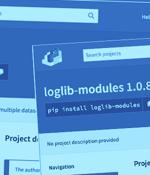
Researchers have discovered a number of malicious Python packages in the official third-party software repository that are engineered to exfiltrate AWS credentials and environment variables to a publicly exposed endpoint. The list of packages includes loglib-modules, pyg-modules, pygrata, pygrata-utils, and hkg-sol-utils, according to Sonatype security researcher Ax Sharma.