Security News > 2022 > January

A new iPhone technique can hijack and prevent any shut-down process that a user initiates, simulating a real power-off while allowing malware to remain active in the background. "The NoReboot approach simulates a real shutdown. The user cannot feel a difference between a real shutdown and a fake shutdown. There is no user-interface or any button feedback until the user turns the phone back 'on'we cannot, and should not, trust a normal reboot."

Attackers are using the "Comments" feature of Google Docs to send malicious links in a phishing campaign targeted primarily at Outlook users, researchers have discovered. Researchers from email collaboration and security firm Avanan, a CheckPoint company, first observed "a new, massive wave of hackers leveraging the comment feature in Google Docs" in December, Avanan Cybersecurity Researcher/Analyst Jeremy Fuchs wrote in a report published Thursday.

A new trend in phishing attacks emerged in December 2021, with threat actors abusing the commenting feature of Google Docs to send out emails that appear trustworthy. Google Docs is used by many employees working or collaborating remotely, so most recipients of these emails are familiar with these notifications.

France's National Commission on Informatics and Liberty, the country's data privacy and protection body, has announced a 60 million euro sanction against Facebook and a 150 million euro penalty against Google. As a result, today CNIL announced an administrative fine of 60 million Euros against Facebook Ireland Ltd. and an additional 100,000 Euros per day of delay of compliance, starting from March 2022.

The Federal Bureau of Investigation says Americans who share their phone number online are being targeted by Google Voice authentication scams. If successful, they will set up a Google Voice account in their victims' names or hijack their Gmail accounts which will later be used in other fraud schemes or in phishing attacks.

The privacy-oriented search engine netted more than 35 billion search queries in 2021, a 46.4% jump over 2020. The company, which bills itself as the "Internet privacy company," offering a search engine and other products designed to "Empower you to seamlessly take control of your personal information online without any tradeoffs," remains a rounding error compared to Google in search.

The framework enables organizations to improve the security and resilience of critical infrastructure with a well-planned and easy-to-use framework. Although the CSF was written and updated while SaaS was on the rise, it is still geared towards the classic legacy critical infrastructure security challenges.

A North Korean cyberespionage group named Konni has been linked to a series of targeted attacks aimed at the Russian Federation's Ministry of Foreign Affairs with New Year lures to compromise Windows systems with malware. The most recent attacks involved the actor gaining access to the target networks through stolen credentials, exploiting the foothold to load malware for intelligence gathering purposes, with early signs of the activity documented by MalwareBytes as far back as July 2021.
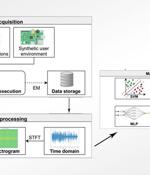
Cybersecurity researchers have proposed a novel approach that leverages electromagnetic field emanations from the Internet of Things devices as a side-channel to glean precise knowledge about the different kinds of malware targeting the embedded systems, even in scenarios where obfuscation techniques have been applied to hinder analysis. With the rapid adoption of IoT appliances presenting an attractive attack surface for threat actors, in part due to them being equipped with higher processing power and capable of running fully functional operating systems, the latest research aims to improve malware analysis to mitigate potential security risks.

In the rush to embrace this new world of work, it's been all too easy to overlook one of the biggest challenges it creates: maintaining cybersecurity. By following a few tips we can stop them in their tracks, and unlock the benefits of a hybrid future of work without sacrificing security.