Security News

Google has released Chrome 103.0.5060.114 for Windows users to address a high-severity zero-day vulnerability exploited by attackers in the wild, the fourth Chrome zero-day patched in 2022. This update was available immediately when BleepingComputer checked for new updates by going into Chrome menu > Help > About Google Chrome.

On Thursday, the Jenkins security team announced 34 security vulnerabilities affecting 29 plugins for the Jenkins open source automation server, 29 of the bugs being zero-days still waiting to be patched. The zero-days' CVSS base scores range from low to high severity, and, according to Jenkins' stats, the impacted plugins have a total of more than 22,000 installs.

A suspected ransomware intrusion against an unnamed target leveraged a Mitel VoIP appliance as an entry point to achieve remote code execution and gain initial access to the environment.The findings come from cybersecurity firm CrowdStrike, which traced the source of the attack to a Linux-based Mitel VoIP device sitting on the network perimeter, while also identifying a previously unknown exploit as well as a couple of anti-forensic measures adopted by the actor on the device to erase traces of their actions.

Hackers used a zero-day exploit on Linux-based Mitel MiVoice VOIP appliances for initial access in what is believed to be the beginning of a ransomware attack. Mitel VOIP devices are used by critical organizations in various sectors for telephony services and were recently exploited by threat actors for high-volume DDoS amplification attacks.
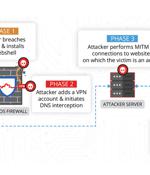
A sophisticated Chinese advanced persistent threat actor exploited a critical security vulnerability in Sophos' firewall product that came to light earlier this year to infiltrate an unnamed South Asian target as part of a highly-targeted attack. "The attacker implement[ed] an interesting web shell backdoor, create[d] a secondary form of persistence, and ultimately launch[ed] attacks against the customer's staff," Volexity said in a report.

Cisco advises owners of end-of-life Small Business RV routers to upgrade to newer models after disclosing a remote code execution vulnerability that will not be patched. According to a Cisco security advisory, the flaw exists due to insufficient user input validation of incoming HTTP packets on the impacted devices.

Timeline May 31: Volexity found zero-day vulnerability in Atlassian Confluence. AI Spera used Criminal IP to determine the number of Atlassian Confluence servers connected to the Internet.

Chinese hackers used a zero-day exploit for a critical-severity vulnerability in Sophos Firewall to compromise a company and breach cloud-hosted web servers operated by the victim.On March 25, Sophos published a security advisory about CVE-2022-1040, an authentication bypass vulnerability that affects the User Portal and Webadmin of Sophos Firewall and could be exploited to execute arbitrary code remotely.

Microsoft claims to have finally fixed the Follina zero-day flaw in Windows as part of its June Patch Tuesday batch, which included security updates to address 55 vulnerabilities. Criminals and snoops can abuse the remote code execution bug, tracked as CVE-2022-30190, by crafting a file, such as a Word document, so that when opened it calls out to the Microsoft Windows Support Diagnostic Tool, which is then exploited to run malicious code, such spyware and ransomware.

Microsoft has released security updates with the June 2022 cumulative Windows Updates to address a critical Windows zero-day vulnerability known as Follina and actively exploited in ongoing attacks. "Microsoft recommends installing the updates as soon as possible," the company further urged customers in a post on the Microsoft Security Response Center.