Security News

Apple has released patches for three zero-day vulnerabilities exploited in the wild. Referencing Kaspersky's findings, Apple says that those last two vulnerabilities "May have been actively exploited against versions of iOS released before iOS 15.7.".

Apple on Wednesday released a slew of updates for iOS, iPadOS, macOS, watchOS, and Safari browser to address a set of flaws it said were actively exploited in the wild. The iPhone maker said it's aware that the two issues "May have been actively exploited against versions of iOS released before iOS 15.7," crediting Kaspersky researchers Georgy Kucherin, Leonid Bezvershenko, and Boris Larin for reporting them.

Apple addressed three new zero-day vulnerabilities exploited in attacks installing Triangulation spyware on iPhones via iMessage zero-click exploits. The attacks started in 2019 and are still ongoing, according to Kaspersky, who reported in early June that some iPhones on its network were infected with previously unknown spyware via iMessage zero-click exploits that exploited iOS zero-day bugs.
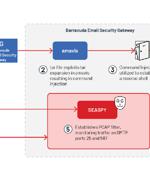
A suspected China-nexus threat actor dubbed UNC4841 has been linked to the exploitation of a recently patched zero-day flaw in Barracuda Email Security Gateway appliances since October 2022. "UNC4841 is an espionage actor behind this wide-ranging campaign in support of the People's Republic of China," Google-owned Mandiant said in a new report published today, describing the group as "Aggressive and skilled."

A suspected pro-China hacker group tracked by Mandiant as UNC4841 has been linked to data-theft attacks on Barracuda ESG appliances using a now-patched zero-day vulnerability. "Due to the sophistication displayed by UNC4841 and lack of full visibility into all compromised appliances, Barracuda has elected to replace and not reimage the appliance from the recovery partition out of an abundance of caution," John Palmisano, Mandiant Incident Response Manager - Google Cloud, told BleepingComputer.

The Chinese state-sponsored group known as UNC3886 has been found to exploit a zero-day flaw in VMware ESXi hosts to backdoor Windows and Linux systems. The VMware Tools authentication bypass vulnerability, tracked as CVE-2023-20867, "Enabled the execution of privileged commands across Windows, Linux, and PhotonOS guest VMs without authentication of guest credentials from a compromised ESXi host and no default logging on guest VMs," Mandiant said.

Hackers are impersonating cybersecurity researchers on Twitter and GitHub to publish fake proof-of-concept exploits for zero-day vulnerabilities that infect Windows and Linux with malware. These malicious exploits are promoted by alleged researchers at a fake cybersecurity company named 'High Sierra Cyber Security,' who promote the GitHub repositories on Twitter, likely to target cybersecurity researchers and firms involved in vulnerability research.

VMware patched today a VMware ESXi zero-day vulnerability exploited by a Chinese-sponsored hacking group to backdoor Windows and Linux virtual machines and steal data.The cyber espionage group-tracked as UNC3886 by cybersecurity firm Mandiant who discovered the attacks-abused the CVE-2023-20867 VMware Tools authentication bypass flaw to deploy VirtualPita and VirtualPie backdoors on guest VMs from compromised ESXi hosts where they escalated privileges to root.

The Clop ransomware gang has been looking for ways to exploit a now-patched zero-day in the MOVEit Transfer managed file transfer solution since 2021, according to Kroll security experts. "Kroll observed activity consistent with MOVEit Transfer exploitation that collectively occurred on April 27, 2022; May 15-16, 2023; and May 22, 2023, indicating that actors were testing access to organizations via likely automated means and pulling back information from the MOVEit Transfer servers to identify which organization they were accessing," the report reveals.

The Clop ransomware gang has been looking for ways to exploit a now-patched zero-day in the MOVEit Transfer managed file transfer solution since 2021, according to Kroll security experts. "Kroll observed activity consistent with MOVEit Transfer exploitation that collectively occurred on April 27, 2022; May 15-16, 2023; and May 22, 2023, indicating that actors were testing access to organizations via likely automated means and pulling back information from the MOVEit Transfer servers to identify which organization they were accessing," the report reveals.