Security News

Cybersecurity expert Kayne McGladrey speaks about why AI cannot do what creative people can, and the important role of generative AI in SOCs. Kayne McGladrey, IEEE Fellow and cybersecurity veteran with more than 25 years of experience, asserts that the human element - particularly people with diverse interests, backgrounds and talents - is irreplaceable in cybersecurity.
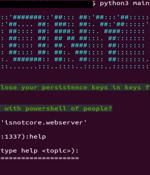
The Iranian state-sponsored group dubbed MuddyWater has been attributed to a previously unseen command-and-control framework called PhonyC2 that's been put to use by the actor since 2021. "MuddyWater is continuously updating the PhonyC2 framework and changing TTPs to avoid detection."

A crypter malware dubbed AceCryptor has been used to pack numerous strains of malware since 2016. Some of the prominent malware families contained within AceCryptor are SmokeLoader, RedLine Stealer, RanumBot, Raccoon Stealer, Stop ransomware, and Amadey, among others.

An unidentified whistleblower has provided several media organizations with access to leaked documents from NTC Vulkan - a Moscow IT consultancy - that allegedly show how the firm supports Russia's military and intelligence agencies with cyber warfare tools. According to The Guardian, this latest whistleblower chose to distribute the secret Russian documents due to anger over Russia's bloody invasion of Ukraine and a desire to see the information reveal some of what is going on inside Russia.
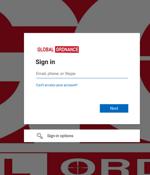
A state-sponsored hacking group with links to Russia has been linked to attack infrastructure that spoofs the Microsoft login page of Global Ordnance, a legitimate U.S.-based military weapons and hardware supplier. The cybersecurity firm said it discovered 38 domains, nine of which contained references to companies like UMO Poland, Sangrail LTD, DTGruelle, Blue Sky Network, the Commission for International Justice and Accountability, and the Russian Ministry of Internal Affairs.

Security researchers have discovered a new campaign targeting multiple military contractors involved in weapon manufacturing, including an F-35 Lightning II fighter aircraft components supplier. The campaign stands out for its secure C2 infrastructure and multiple layers of obfuscation in the PowerShell stagers.

Several weapon marketplaces on the dark web have listed military-grade firearms allegedly coming from Western countries that sent them to support the Ukrainian army in its fight against the Russian invaders. While the listings appear genuine and the offered weapons are priced realistically, the chances of them being created by pro-Russian actors for propaganda purposes are high.

Several weapon marketplaces on the dark web have listed military-grade firearms allegedly coming from Western countries that sent them to support the Ukrainian army in its fight against the Russian invaders. While the listings appear genuine and the offered weapons are priced realistically, the chances of them being created by pro-Russian actors for propaganda purposes are high.

China claims it has obtained a sample of malware used by the NSA to steal files, monitor and redirect network traffic, and remotely control computers to spy on foreign targets. The NSA apparently used NOPEN to take over "a large number" of computers around the world, and the theft of data from this equipment has caused "Inestimable losses," the tabloid reported.

The REvil ransomware gang, thought to be behind an attack on meat producer JBS which netted an impressive $11m payoff, has found another victim. Described as a "a small, veteran-owned consulting firm focused on managing advanced technologies and concepts with strong potential for military and space applications," Sol Oriens' links to the US nuclear weapons programme were revealed in a job posting for a "Senior Nuclear Weapons System Subject Matter Expert" on recruitment site Lensa, first spotted by CNBC correspondent Eamon Javers.