Security News > 2023 > June > From MuddyC3 to PhonyC2: Iran's MuddyWater Evolves with a New Cyber Weapon
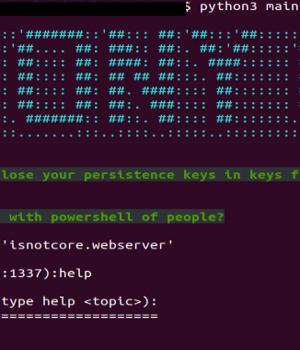
The Iranian state-sponsored group dubbed MuddyWater has been attributed to a previously unseen command-and-control framework called PhonyC2 that's been put to use by the actor since 2021.
"MuddyWater is continuously updating the PhonyC2 framework and changing TTPs to avoid detection."
"Iran conducts cyber operations aiming at intelligence collection for strategic purposes, essentially targeting neighboring states, in particular Iran's geopolitical rivals such as Israel, Saudi Arabia, and Arabic Gulf countries, a continued focus observed in all operations since 2011," French cybersecurity company Sekoia said in an overview of pro-Iranian government cyber attacks.
Deep Instinct said it discovered the PhonyC2 framework in April 2023 on a server that's related to broader infrastructure put to use by MuddyWater in its attack targeting Technion earlier this year.
The connection stems from the artifact names "C:programdatadb.sqlite" and "C:programdatadb.ps1," which Microsoft described as customized PowerShell backdoors used by MuddyWater and which are dynamically generated via the PhonyC2 framework for execution on the infected host.
PhonyC2 is a "Post-exploitation framework used to generate various payloads that connect back to the C2 and wait for instructions from the operator to conduct the final step of the 'intrusion kill chain,'" Kenin said, calling it a successor to MuddyC3 and POWERSTATS. Some of the the notable commands supported by the framework are as follows -.
News URL
https://thehackernews.com/2023/06/from-muddyc3-to-phonyc2-irans.html