Security News

Threat actors are actively exploiting a recently disclosed critical security flaw impacting Apache HugeGraph-Server that could lead to remote code execution attacks. It has been described as a remote command execution flaw in the Gremlin graph traversal language API. "Users are recommended to upgrade to version 1.3.0 with Java11 and enable the Auth system, which fixes the issue," the Apache Software Foundation noted in late April 2024.

Exclusive A Microsoft zero-day exploit that Trend Micro's Zero Day Initiative team claims it found and reported to Redmond in May was disclosed and patched by the Windows giant in July's Patch Tuesday - but without any credit given to ZDI. The flaw, tracked as CVE-2024-38112, is in MSHTML - Microsoft's proprietary browser engine for Internet Explorer. This entire series of unfortunate events not only highlights problems with Microsoft's bug reporting program, but also the coordinated vulnerability disclosure process in general, according to Childs.

The maintainers of the Exim mail transfer agent have fixed a critical vulnerability that currently affects around 1.5 million public-facing servers and can help attackers deliver malware to users. CVE-2024-39929 affects Exim releases up to and including 4.97.1, and has been fixed in Exim v4.98, which was released last week.

A critical security issue has been disclosed in the Exim mail transfer agent that could enable threat actors to deliver malicious attachments to target users' inboxes. "Exim through 4.97.1 misparses a multiline RFC 2231 header filename, and thus remote attackers can bypass a $mime filename extension-blocking protection mechanism, and potentially deliver executable attachments to the mailboxes of end users," according to a description shared on the U.S. National Vulnerability Database.

A BlastRADIUS attack involves the attacker intercepting network traffic between a client, such as a router, and the RADIUS server. While MD5 is well-known to have weaknesses that allow attackers to generate collisions or reverse the hash, the researchers say that the BlastRADIUS attack "Is more complex than simply applying an old MD5 collision attack" and more advanced in terms of speed and scale.
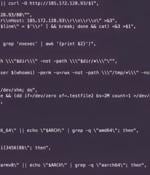
The vulnerability in question is CVE-2024-4577, which allows an attacker to remotely execute malicious commands on Windows systems using Chinese and Japanese language locales. The disclosure comes as Cloudflare said it recorded a 20% year-over-year increase in DDoS attacks in the second quarter of 2024, and that it mitigated 8.5 million DDoS attacks during the first six months.

The Blast-RADIUS attack allows a man-in-the-middle attacker between the RADIUS client and server to forge a valid protocol accept message in response to a failed authentication request. This forgery could give the attacker access to network devices and services without the attacker guessing or brute forcing passwords or shared secrets.
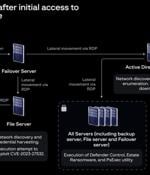
A now-patched security flaw in Veeam Backup & Replication software is being exploited by a nascent ransomware operation known as EstateRansomware. "Before the ransomware attack, there were VPN brute-force attempts noted in April 2024 using a dormant account identified as 'Acc1.' Several days later, a successful VPN login using 'Acc1' was traced back to the remote IP address 149.28.106[.]252.".

Select versions of the OpenSSH secure networking suite are susceptible to a new vulnerability that can trigger remote code execution. The vulnerability, tracked as CVE-2024-6409, is distinct from CVE-2024-6387 and relates to a case of code execution in the privsep child process due to a race condition in signal handling.

Cybersecurity researchers have discovered a security vulnerability in the RADIUS network authentication protocol called BlastRADIUS that could be exploited by an attacker to stage Mallory-in-the-middle attacks and bypass integrity checks under certain circumstances. "The RADIUS protocol allows certain Access-Request messages to have no integrity or authentication checks," InkBridge Networks CEO Alan DeKok, who is the creator of the FreeRADIUS Project, said in a statement.