Security News

The internet-facing assets were found to be susceptible to potential exploitation in a sample of 90 banking and financial services organisations.

The most dangerous vulnerability you’ve never heard of. In the world of cybersecurity, vulnerabilities are discovered so often, and at such a high rate, that it can be very difficult to keep up...
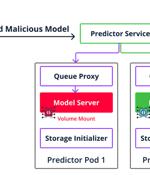
Cybersecurity researchers are warning about the security risks in the machine learning (ML) software supply chain following the discovery of more than 20 vulnerabilities that could be exploited to...

Vulnerabilities in popular Microsoft apps for macOS can be abused by attackers to record video and audio clips, take pictures, access and exfiltrate data and send emails, Cisco Talos researchers have discovered. Library injection vulnerabilities in Microsoft apps for macOS. The flaws - CVE-2024-41138, CVE-2024-41145, CVE-2024-41159, CVE-2024-42004, CVE-2024-41165, CVE-2024-43106, CVE-2024-39804 and CVE-2024-42220 - have been found in Microsoft Teams, OneNote, Outlook, Word, Excel and Powerpoint for macOS. They allow attackers to inject specially crafted libraries so they can assume the vulnerable apps' entitlements and the permissions they've been granted by users.

Cybersecurity researchers have discovered two security flaws in Microsoft's Azure Health Bot Service that, if exploited, could permit a malicious actor to achieve lateral movement within customer environments and access sensitive patient data. The critical issues, now patched by Microsoft, could have allowed access to cross-tenant resources within the service, Tenable said in a new report shared with The Hacker News.

Cybersecurity researchers have identified a number of security shortcomings in photovoltaic system management platforms operated by Chinese companies Solarman and Deye that could enable malicious actors to cause disruption and power blackouts. "If exploited, these vulnerabilities could allow an attacker to control inverter settings that could take parts of the grid down, potentially causing blackouts," Bitdefender researchers said in an analysis published last week.
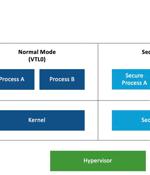
Microsoft said it is developing security updates to address two loopholes that it said could be abused to stage downgrade attacks against the Windows update architecture and replace current versions of the Windows files with older versions. The second vulnerability also concerns a case of privilege escalation in Windows systems that support VBS, effectively allowing an adversary to replace current versions of Windows system files with outdated versions.

A researcher has developed a downgrade attack that can make Windows machines covertly, persistently and irreversibly vulnerable, even if they were fully patched before that. A downgrade attack exploiting the Windows Update process.

The study uncovered that OT and IoT cellular routers and those used in small offices and homes contain outdated software components associated with known vulnerabilities. The research showed that widely used OT/IoT router firmware images have, on average, 20 exploitable n-day vulnerabilities affecting the kernel, leading to increasing security risks.

The Internet Systems Consortium (ISC) has released patches to address multiple security vulnerabilities in the Berkeley Internet Name Domain (BIND) 9 Domain Name System (DNS) software suite that...