Security News

The maintainers of the open-source file-sharing software ownCloud have warned of three critical security flaws that could be exploited to disclose sensitive information and modify files. A brief...

In a rare squid/security post, here's an article about unpatched vulnerabilities in the Squid caching proxy. As usual, you can also use this squid post to talk about the security stories in the news that I haven't covered.

Microsoft has released fixes to address 63 security bugs in its software for the month of November 2023, including three vulnerabilities that have come under active exploitation in the wild. Of...

Google joins OpenAI and Microsoft in rewarding AI bug hunts. Google expanded its Vulnerability Rewards Program to include bugs and vulnerabilities that could be found in generative AI. Specifically, Google is looking for bug hunters for its own generative AI, products such as Google Bard, which is available in many countries, or Google Cloud's Contact Center AI, Agent Assist.
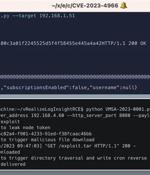
Virtualization services provider VMware has alerted customers to the existence of a proof-of-concept (PoC) exploit for a recently patched security flaw in Aria Operations for Logs. Tracked as...

Cisco has patched two zero-day vulnerabilities that exposed Cisco IOS XE system software hosts to attackers. These vulnerabilities affected devices running the Cisco IOS XE software, such as routers and switches.

In the pursuit of optimized performance, modern compilers employ sophisticated techniques, translating high-level source code into efficient, executable programs. Unbeknownst to many, these obscure threats can counteract safety measures and render a seemingly secure application vulnerable post-compilation.
Two critical security flaws discovered in the open-source CasaOS personal cloud software could be successfully exploited by attackers to achieve arbitrary code execution and take over susceptible...

The U.S. Cybersecurity and Infrastructure Security Agency has unveiled additional details regarding misconfigurations and security vulnerabilities exploited by ransomware gangs, aiming to help critical infrastructure organizations thwart their attacks. Since its inception, CISA's RVWP has identified and shared details of over 800 vulnerable systems with internet-accessible vulnerabilities frequently targeted by various ransomware operations.

Described by curl project founder and lead developer Daniel Stenberg as "Probably the worst curl security flaw in a long time," the patches address two separate vulnerabilities: CVE-2023-38545 and CVE-2023-38546. We now know the first vulnerability, CVE-2023-38545, is a heap-based buffer overflow flaw that affects both libcurl and the curl tool, carrying a severity rating of "High." Possible outcomes of such issues include the corruption of data and, in the worst cases, the execution of arbitrary code.