Security News

Veeam has fixed two vulnerabilities in Veeam Service Provider Console (VSPC), one of which (CVE-2024-42448) may allow remote attackers to achieve code exection on the VSPC server machine. The...

After being used in Akira and Fog ransomware attacks, a critical Veeam Backup & Replication (VBR) security flaw was also recently exploited to deploy Frag ransomware. [...]

Threat actors are actively attempting to exploit a now-patched security flaw in Veeam Backup & Replication to deploy Akira and Fog ransomware. Cybersecurity vendor Sophos said it has been tracking...

Ransomware gangs now exploit a critical security vulnerability that lets attackers gain remote code execution (RCE) on vulnerable Veeam Backup & Replication (VBR) servers. [...]

Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Veeam Backup & Replication RCE flaw may soon be leveraged by ransomware gangs (CVE-2024-40711)...

CVE-2024-40711, a critical vulnerability affecting Veeam Backup & Replication (VBR), could soon be exploited by attackers to steal enterprise data. Discovered and reported by Code WHite researcher...

Veeam has shipped security updates to address a total of 18 security flaws impacting its software products, including five critical vulnerabilities that could result in remote code execution. The...

Veeam has released security updates for several of its products as part of a single September 2024 security bulletin that addresses 18 high and critical severity flaws in Veeam Backup &...

Another new ransomware gang, this one dubbed EstateRansomware, is exploiting a Veeam vulnerability that was patched more than a year ago to drop file-encrypting malware, a LockBit variant, and extort payments from victims. Veeam fixed the flaw, tracked as CVE-2023-27532, in March 2023 for versions 12/11a and later of its backup and replication software.
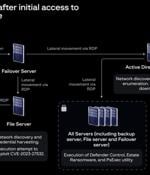
A now-patched security flaw in Veeam Backup & Replication software is being exploited by a nascent ransomware operation known as EstateRansomware. "Before the ransomware attack, there were VPN brute-force attempts noted in April 2024 using a dormant account identified as 'Acc1.' Several days later, a successful VPN login using 'Acc1' was traced back to the remote IP address 149.28.106[.]252.".