Security News
Malicious Google Search ads for generative AI services like OpenAI ChatGPT and Midjourney are being used to direct users to sketchy websites as part of a BATLOADER campaign designed to deliver RedLine Stealer malware. BATLOADER is a loader malware that's propagated via drive-by downloads where users searching for certain keywords on search engines are displayed bogus ads that, when clicked, redirect them to rogue landing pages hosting malware.

AppSec teams are stuck in a catch-up cycle, unable to keep up with the increasingly rapid, agile dev pace, and playing security defense via an endless and unproductive vulnerability chase, according to Backslash Security. Far and wide, enterprises are victims of this costly 'defensive tax:' the cost of employing AppSec engineers who chase vulnerabilities rather than drive a comprehensive cloud-native AppSec program is estimated to be upwards of $1.2 million annually.

Using commonly available tools allows attackers to evade detection. While custom-built tools or malware can be flagged as malicious by endpoint products, commercially available tools are often marked as clean or allow-listed by organizations.
Product security teams aim to guarantee the intrinsic reliability of applications. In the DevSecOps approach, each team is responsible for the security of the applications they create.

The report found that a majority of modern phishing attacks rely on stolen credentials and outlined the growing threat from Adversary-in-the-Middle attacks, increased use of the InterPlanetary File System, as well as reliance on phishing kits sourced from black markets and AI tools like ChatGPT. "Phishing remains one of the most prevalent threat vectors cybercriminals utilize to breach global organizations. Year-over-year, we continue to see an increase in the number of phishing attacks which are becoming more sophisticated in nature. Threat actors are leveraging phishing kits & AI tools to launch highly effective e-mail, SMiShing, and Vishing campaigns at scale"," said Deepen Desai, Global CISO and Head of Security, Zscaler. "AitM attacks supported by growth in Phishing-as-a-Service have allowed attackers to bypass traditional security models, including multi-factor authentication. To protect their environment, organizations should adopt a zero trust architecture to significantly minimize the attack surface, prevent compromise, and reduce the blast radius in case of a successful attack," added Desai.

Balancing cybersecurity with business priorities: Advice for BoardsIn this Help Net Security interview, Alicja Cade, Director, Financial Services, Office of the CISO, Google Cloud, offers insights on how asking the right questions can help improve cyber performance and readiness, advance responsible AI practices, and balance the need for cybersecurity with other business priorities. 5 free online cybersecurity resources for small businessesThis article will explore five free resources that small companies can leverage to improve their cybersecurity posture without breaking the bank.

The Log4Shell hole was a security flaw in the logging process itself, and boiled down to the fact that many logfile systems allow you to write what almost amount to "Mini-programs" right in the middle of the text that you want to log, in order to make your logfiles "Smarter" and easier to read. For example, if you asked Log4J to log the text I AM DUCK, Log4J would do just that. This time round, the logging-related bug we're warning you about is CVE-2023-20864, a security hole in VMWare's Aria Operations for Logs product.

Across all BEC attacks seen over the past year, 57% relied on language as the main attack vector to get them in front of unsuspecting employees, according to Armorblox. Language remains the main attack vector in BEC attacks.

Integrating the Local Administrator Password Solution into Windows and Windows Server that came with updates earlier this week is causing interoperability problems with what's called legacy LAPS, Microsoft says. Redmond touted the LAPS integration in the April 11 KB5025224 and KB5025239 cumulative updates, writing that "Windows LAPS is a huge improvement in virtually every area beyond Legacy LAPS.".
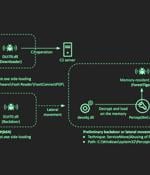
The North Korean threat actor known as the Lazarus Group has been observed shifting its focus and rapidly evolving its tools and tactics as part of a long-running activity called DeathNote. The targeting of the automotive and academic verticals is tied to Lazarus Group's broader attacks against the defense industry, as documented by the Russian cybersecurity firm in October 2021, leading to the deployment of BLINDINGCAN and COPPERHEDGE implants.