Security News

Here's why: the OMB directs government organizations to focus on standalone systems that are connected to critical infrastructure or sensitive information but neglects a key area - the web applications that the private sector has depended on to conduct business for years. Web applications are often deeply integrated and widely accessed within companies, defying the neatly defined security borders of the standalone systems targeted by the OMB. Neglecting web application security therefore neglects a significant area of cyber risk for companies.

In a survey by BlueVoyant, 97% of people said they've been impacted by a security breach that occurred in their supply chain. How do you combat something over which you seemingly have little or no control? A report by cybersecurity provider BlueVoyant looks at supply chain security breaches and offers tips on how to prevent them.

Over the second quarter of the year, 73% of ransomware detections were related to the REvil/Sodinokibi family, while Darkside attacks expanded to more industries, McAfee says. In its latest Advanced Threat Research Report, McAfee looks at the most prominent ransomware strains for the second quarter of 2021 and offers advice on how to combat them.

Iran, Turkey and both North and South Korea are bases for nation-state cyber attacks, Microsoft has claimed - as well as old favourite Russia. "After Russia, the largest volume of attacks we observed came from North Korea, Iran and China; South Korea, Turkey and Vietnam were also active but represent much less volume," said MS in a post announcing its findings.

The addition of Reveal(x) Advisor services to the Reveal(x) 360 network detection and response tools helps organizations proactively manage cybersecurity hygiene and accelerate incident response. ExtraHop announced Tuesday expanded Reveal(x) Advisor services to include threat detection and threat hunting services as well as network assurance analysis.

Attivo Networks announced the availability of a research report conducted by Enterprise Management Associates which focuses on Active Directory, exploring the obstacles and threats organizations face when protecting AD and how they adapt to address these growing concerns. As evidence of the value that attackers place in exploiting Active Directory and the privileges it contains, the report revealed that 50% of organizations experienced an attack on Active Directory in the last 1-2 years, with over 40% indicating the attack was successful.

While there is a time and place for onboarding additional cloud security solutions, it can also be easy to fall prey to the shiny object syndrome surrounding emerging solutions that are created in response to new security threats. Before rushing to invest in a new solution remember that matching additional solutions to emerging threats in a one-to-one game of whack-a-mole is not a sustainable strategy.

Leveraging threat intelligence to tackle supply chain vulnerabilitiesIn this interview with Help Net Security, Brandon Hoffman, CISO at Intel 471, talks about the growing threat of supply chain attacks, the most common supply chain vulnerabilities and how the right threat intelligence can help stay on top of these threats. 3 ways any company can guard against insider threats this OctoberOctober is Cybersecurity Awareness Month, but most business leaders and consumers don't need a special event to remember cybersecurity's preeminence in today's turbulent digital landscape.
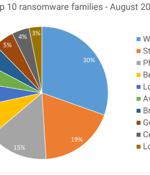
Move over REvil, Ragnar Locker, BlackMatter, Conti et al: Three lesser-known gangs account for the vast majority of ransomware attacks in the U.S. and globally. While there seem to be legions of ransomware gangs, it turns out that just a handful of ransomware-as-a-service actors dominate the entire ecosystem of encryption-attack threats.

Security specialist ESET's latest Threat Report warns of a massive increase in attacks on Remote Desktop Protocol endpoints - and new activity from the Nobelium gang against European government organisations. ESET's figures show attacks on RDP servers having gone up 103.9 per cent since its T1 report in June - it publishes three a year - representing a total of 55 billion detected brute-force attacks, thanks in no small part to a campaign focused on Spanish targets.